OceanStor Integration with RSA SecurID + Test Report

1 Background
Domain users can be configured on Device Manager, and the authentication methods that LDAP users can use are divided into: « login password » and « login password + RADIUS dynamic password ». The RADIUS user authentication method is RADIUS dynamic password (RADIUS users are only available for Dorado.) 6.1.5 and later). RADIUS when used for RSA SecurID built-in RADIUSThe dynamic password needs to be filled in according to the RSA configuration method: TOKEN, PIN followed TOKEN and PINPad.
2 Test Environment
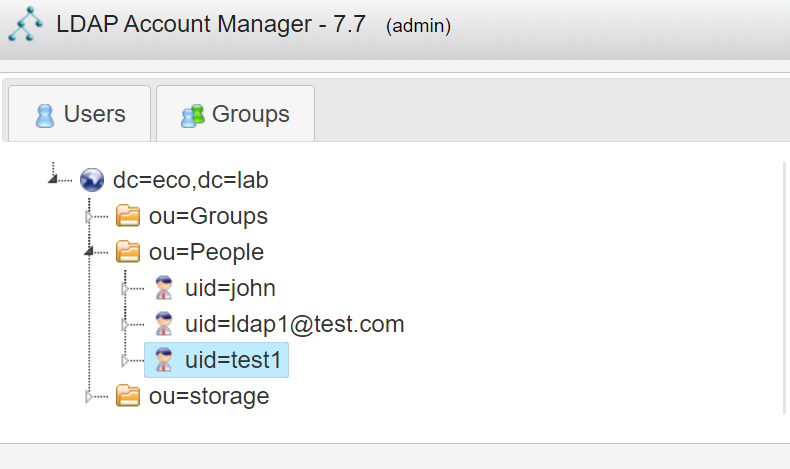
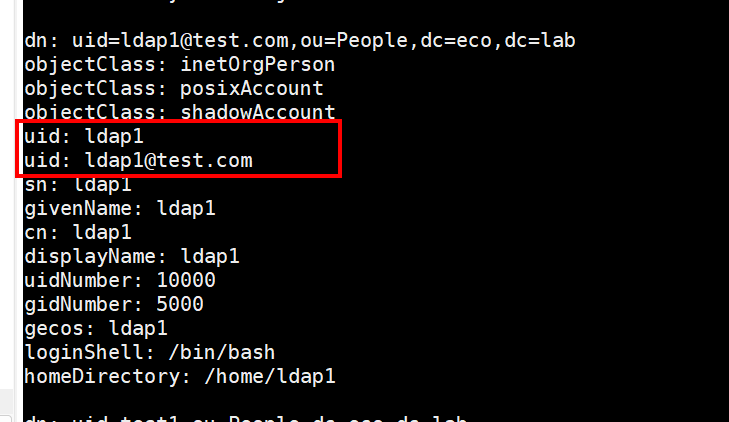
LDAP server: OpenLDAP, the created user is shown below
RADIUS server: RSA SecurID
Storage: OceanStor Dorado 8000 V6 6.1.6
LDAP servers, RSA servers, and storage must be able to ping each other
3 Integration Procedure
3.1 Configure the RADIUS server on RSA SecurID to create a user
1) The admin user logs in to RSA Security Console, https:// IP address/scThe radius server address is the RSA AM server address.
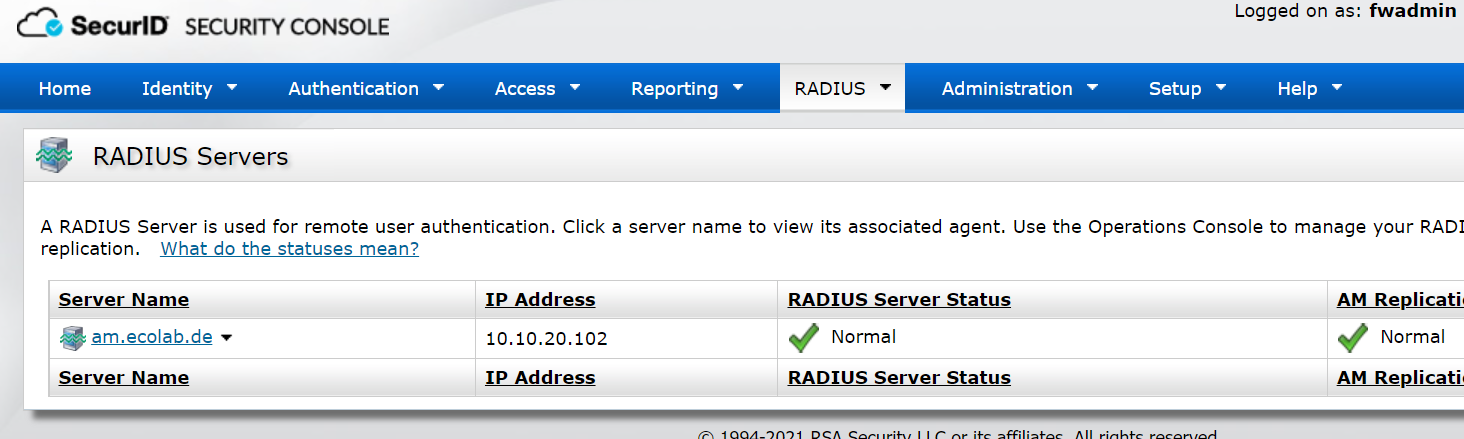
2) Create a Radius client
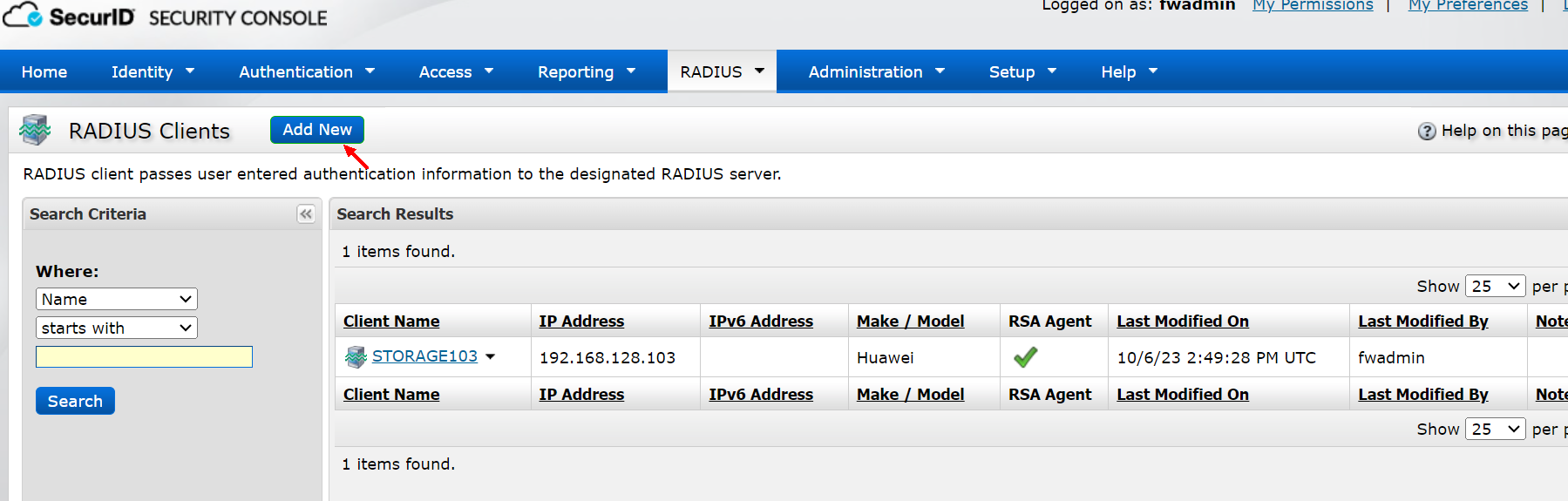
Theip address fills in the storage address, the secret is required for subsequent configuration of storage, and finally select save&create Associated RSA Agent
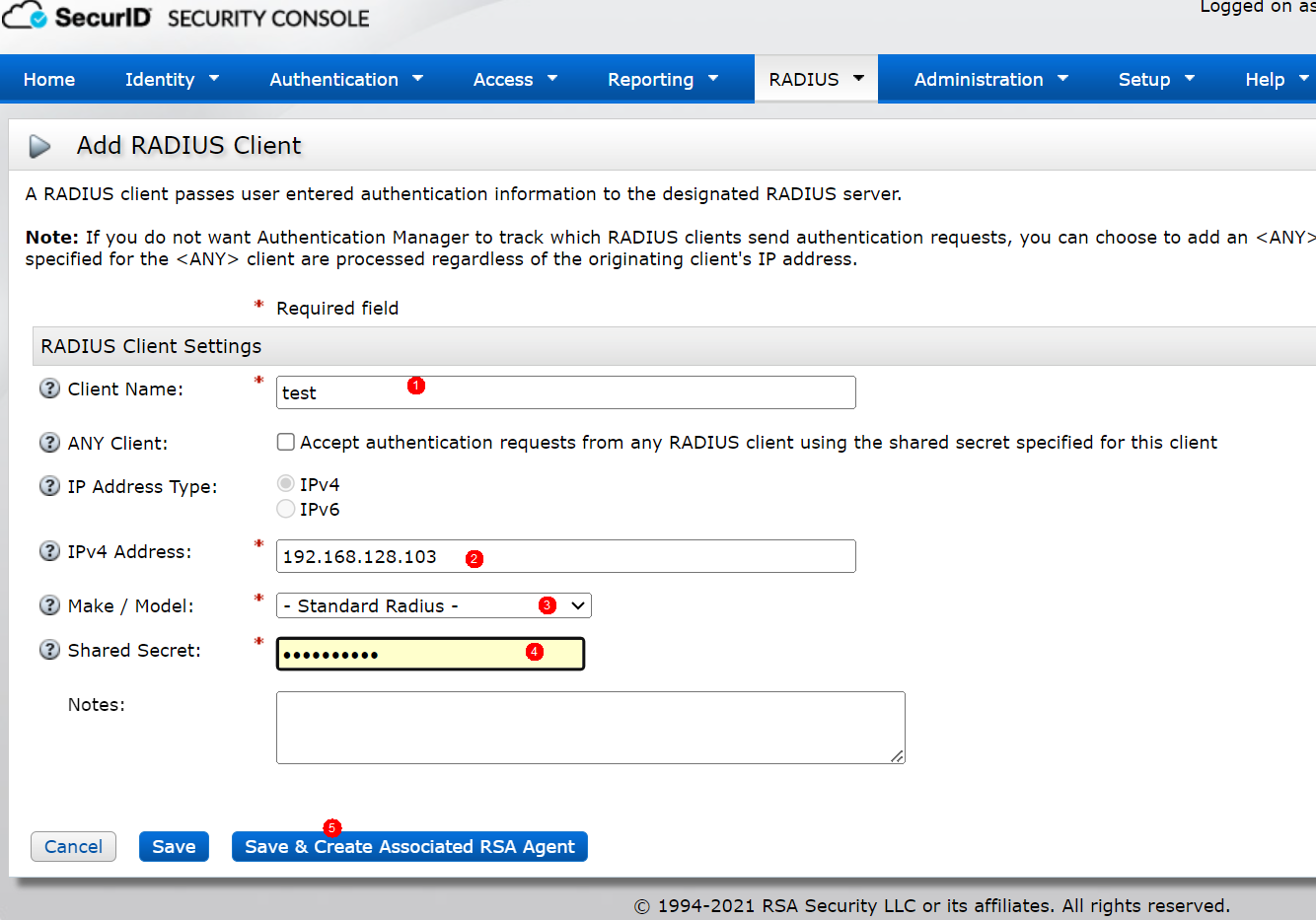
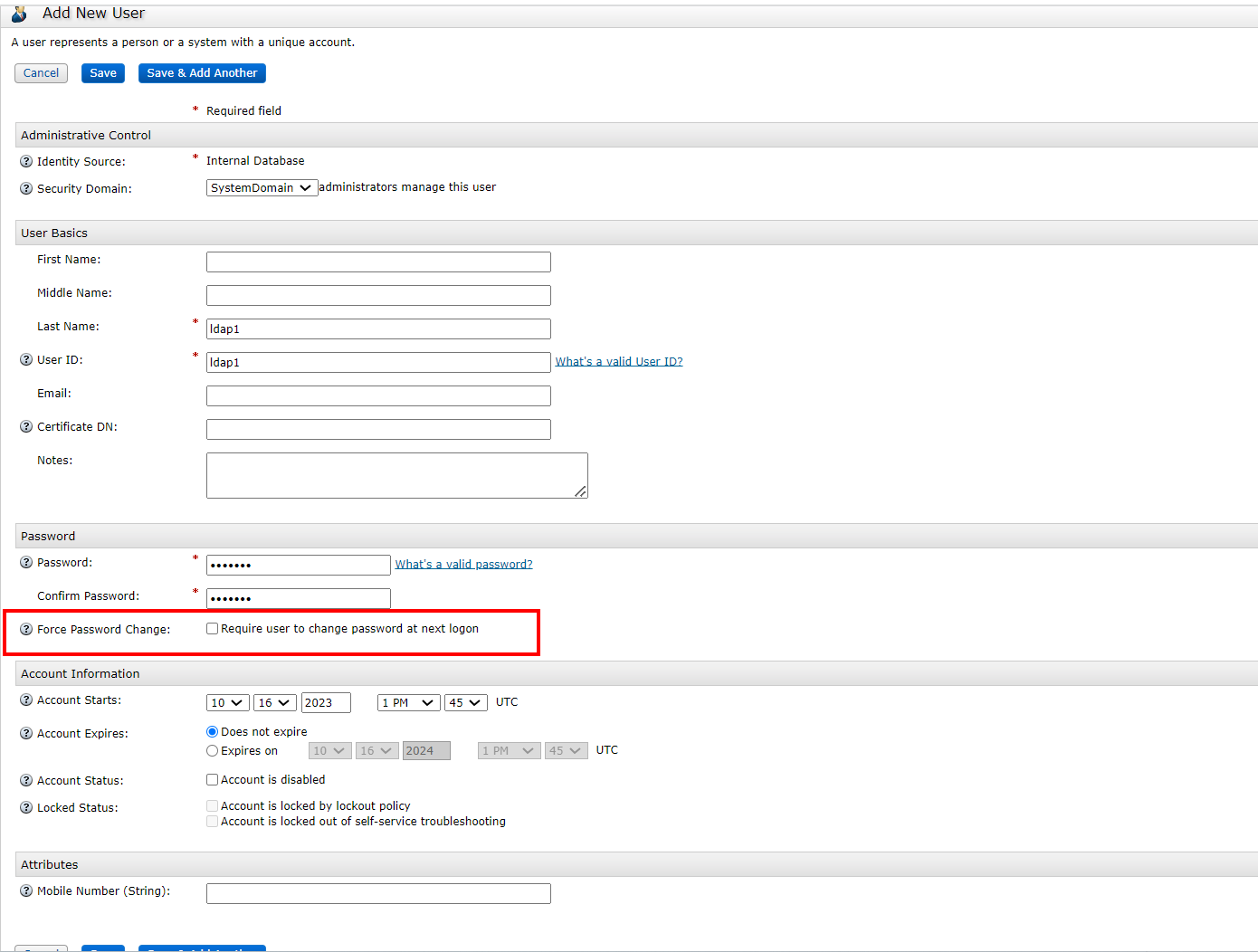
3) Create a user, if you are an LDAP user, you need a RADIUS dynamic password to log in, and the user name when creating the user must be the same as the user configured in the LDAP server.
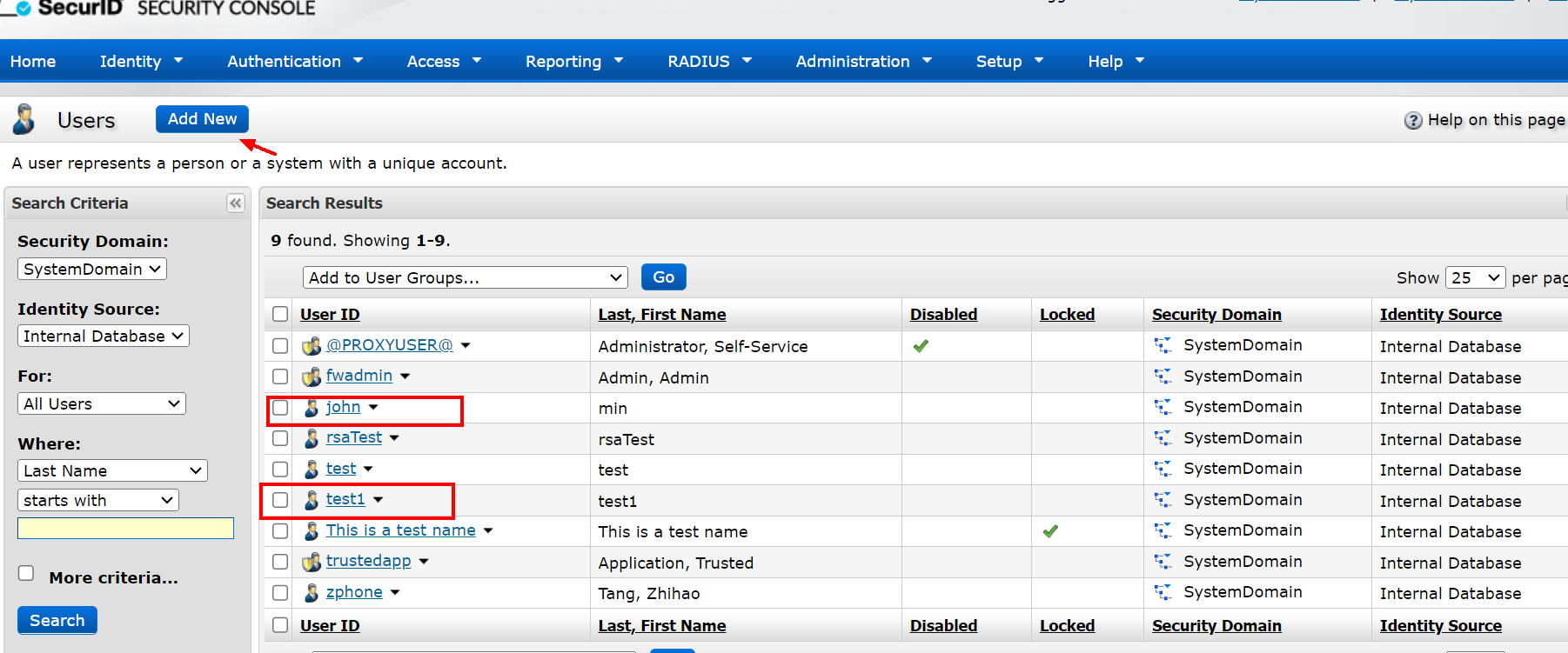
Create a user with the same name, LDAP1
3.2 Configure RADIUS & LDAP on OceanStor
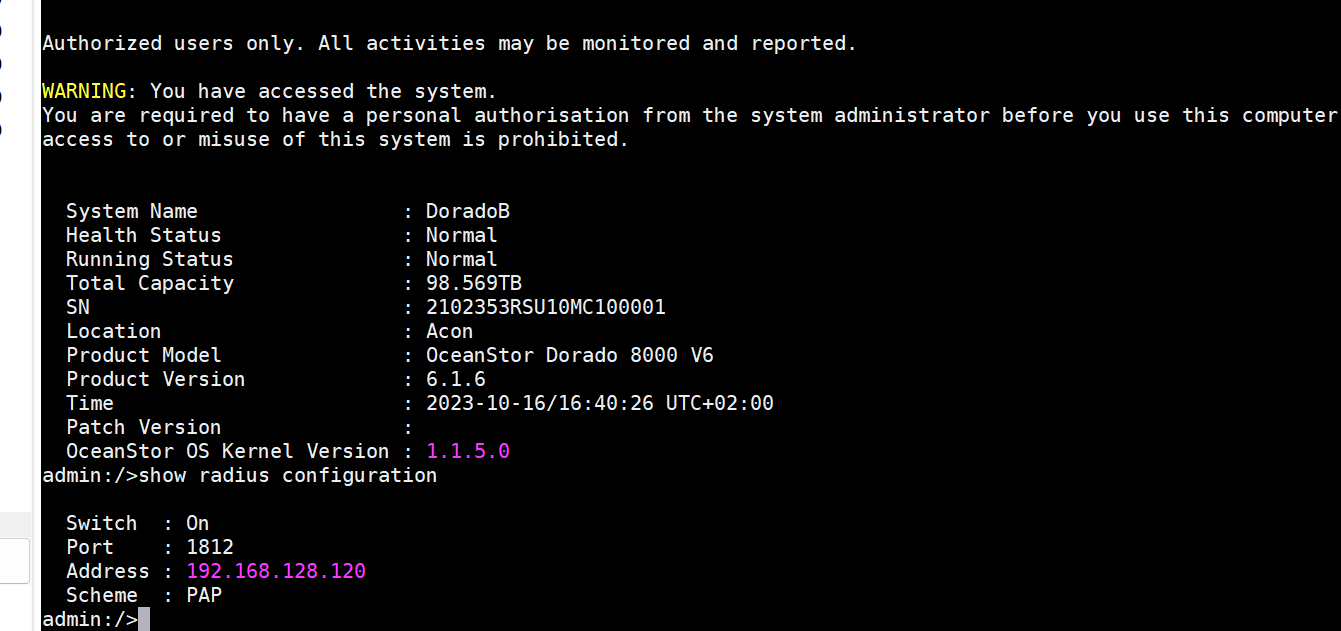
The admin user logs in to the store and runs the following command, where address is the radius server address, and scheme can choose PAP or CHAPThe secret is the same as the secret set by the radius client on RSA.
change radius configuration switch=on address=xxxx port=1812 scheme=xxxx secret=xxxx
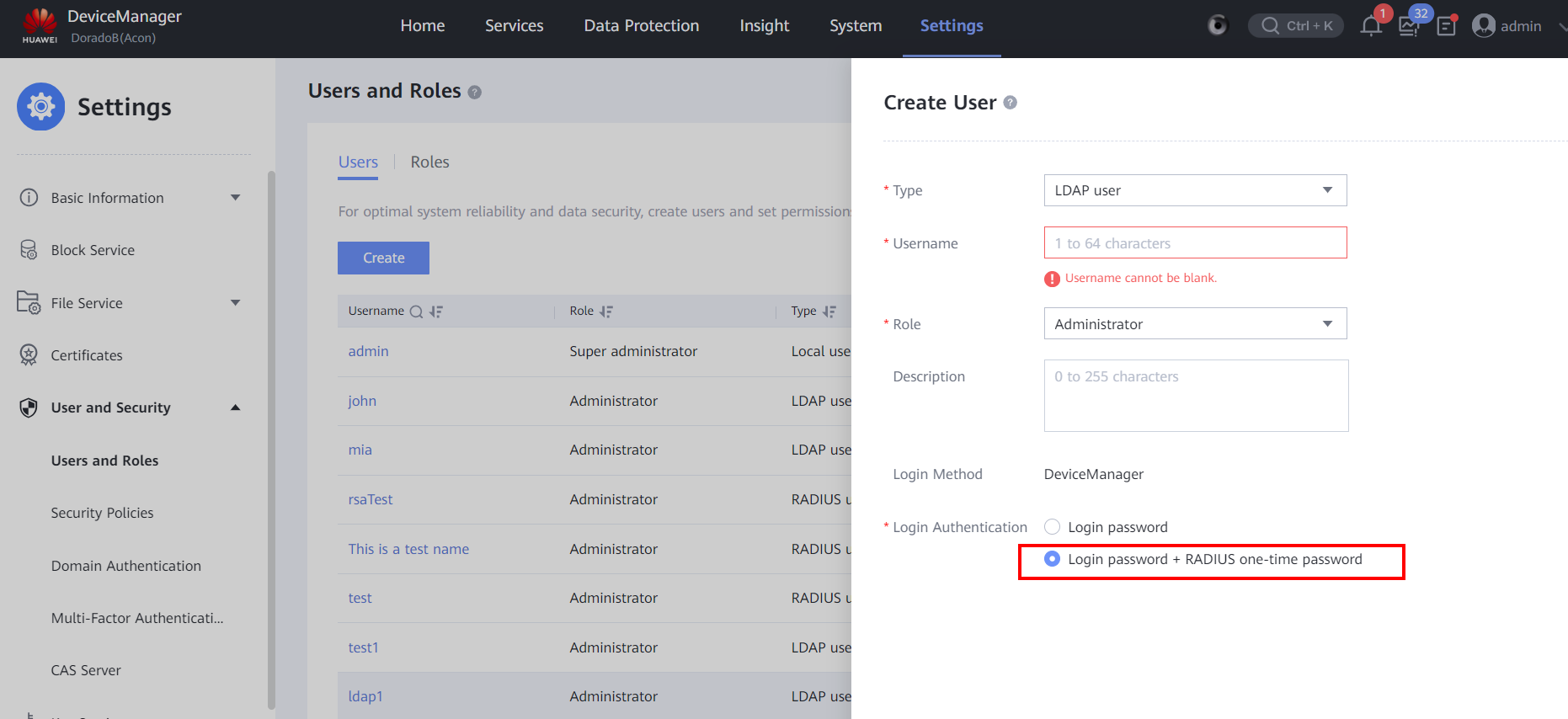
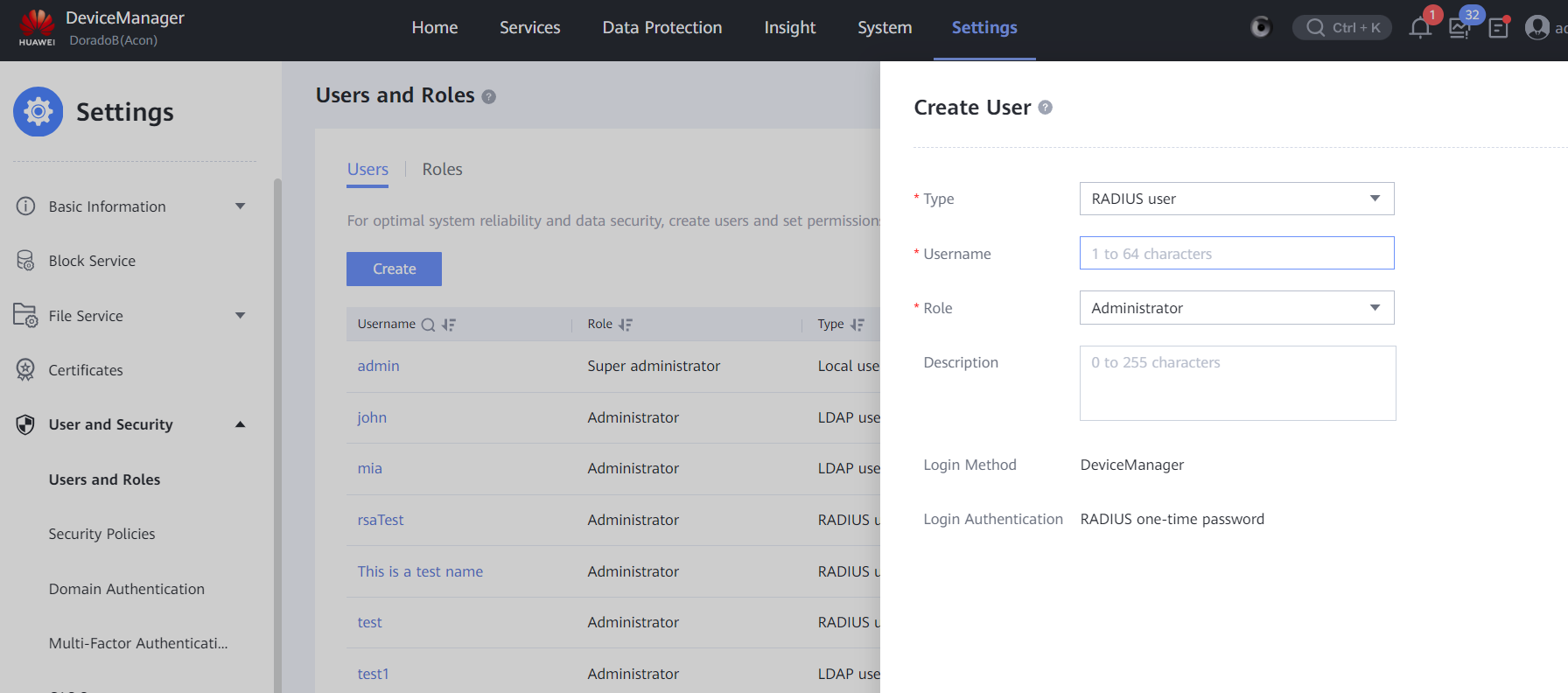
3.3 LDAP + SecureID+ (PIN followed by TOKEN)
1) Create Token Profiles, Authentication>Software Token Profiles> Manage Existing> Add New
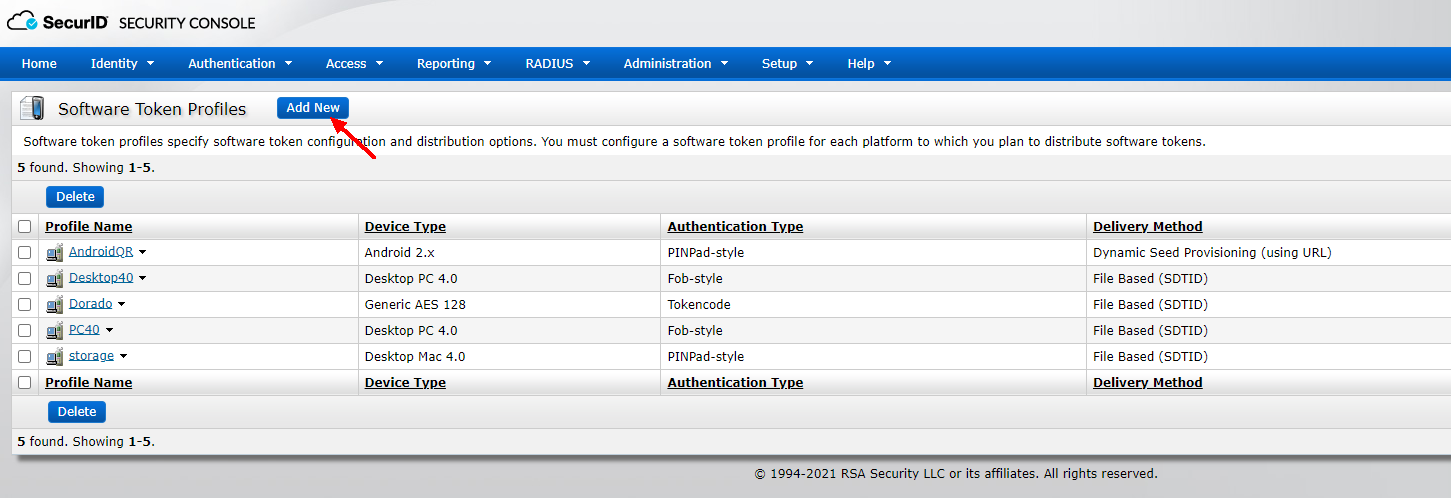
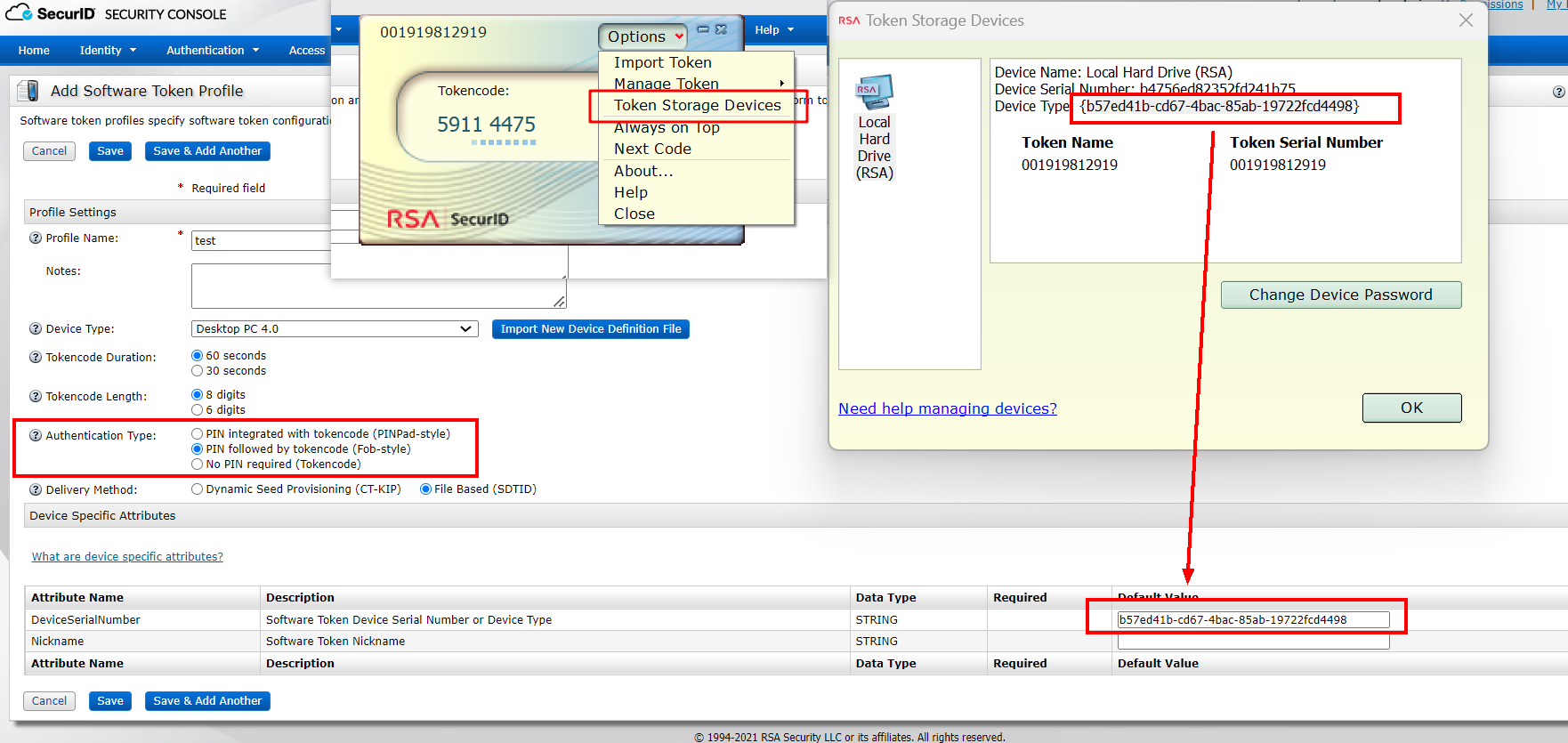
Authentication Type: Select the authentication method, and the value of DeviceSerialNumber: RSA SecurID Token is saved
2) Assign tokens to users
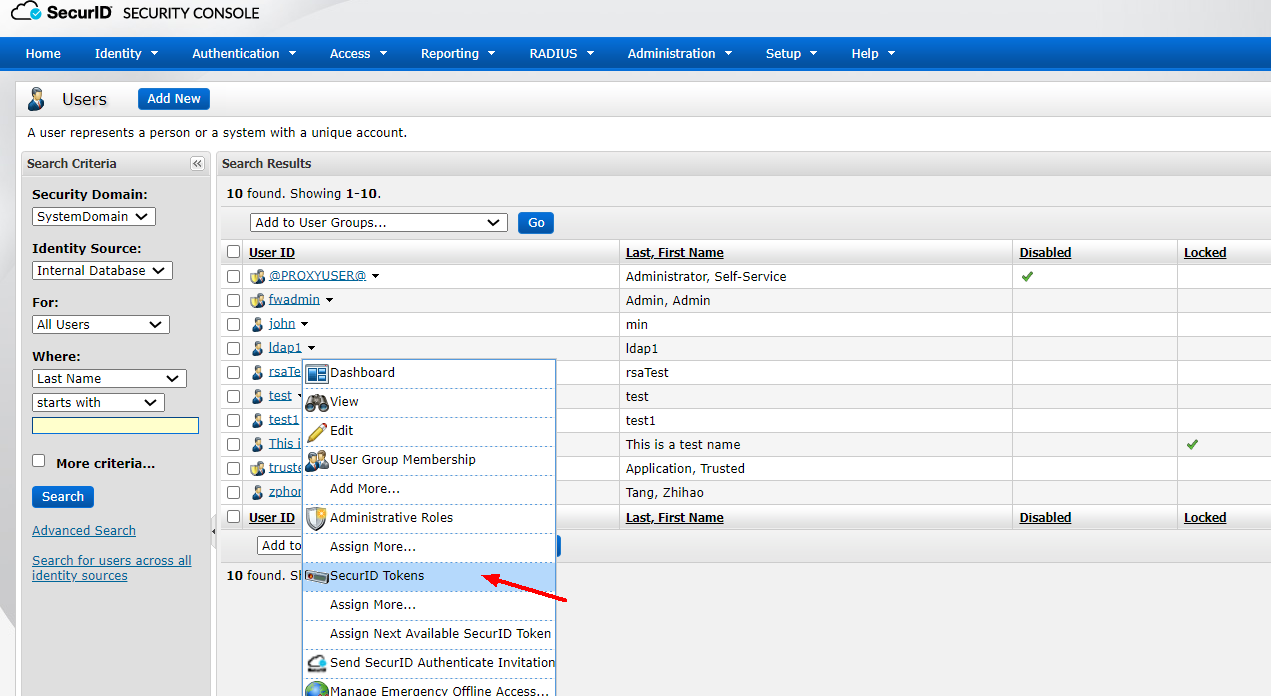
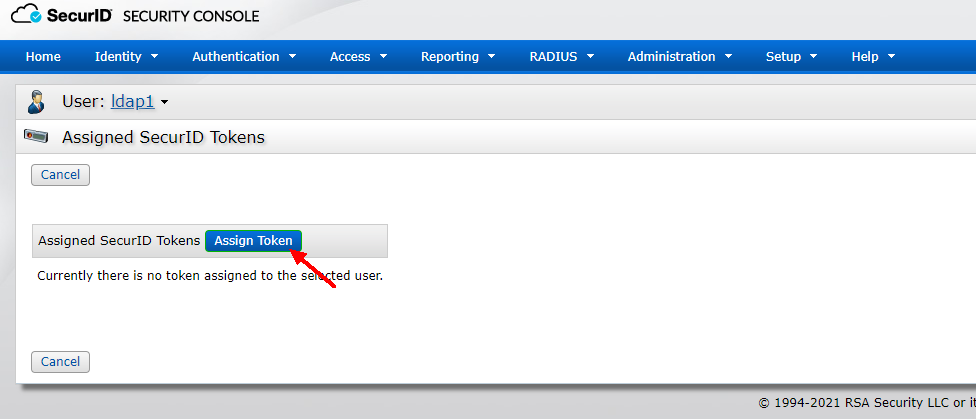
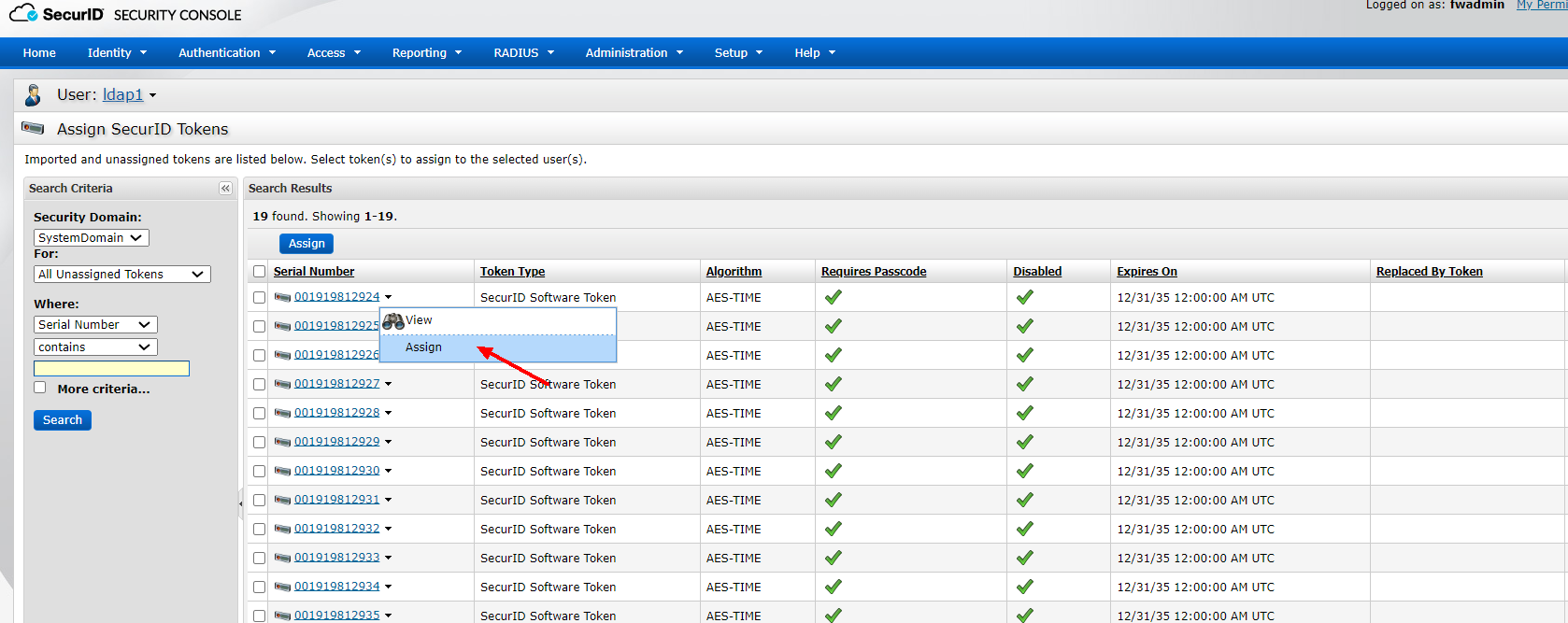
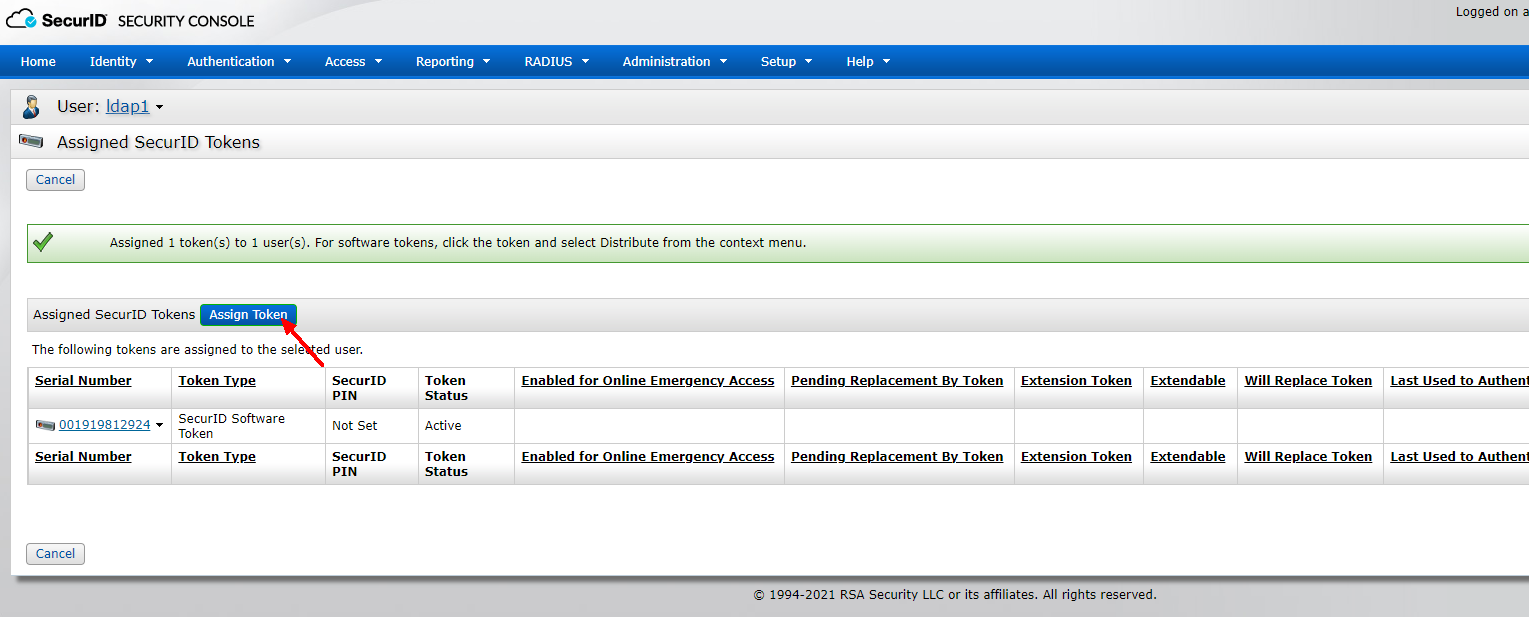
After successfully assigning tokens, SecurID Tokens >Manage Existing find the token of user ldap1
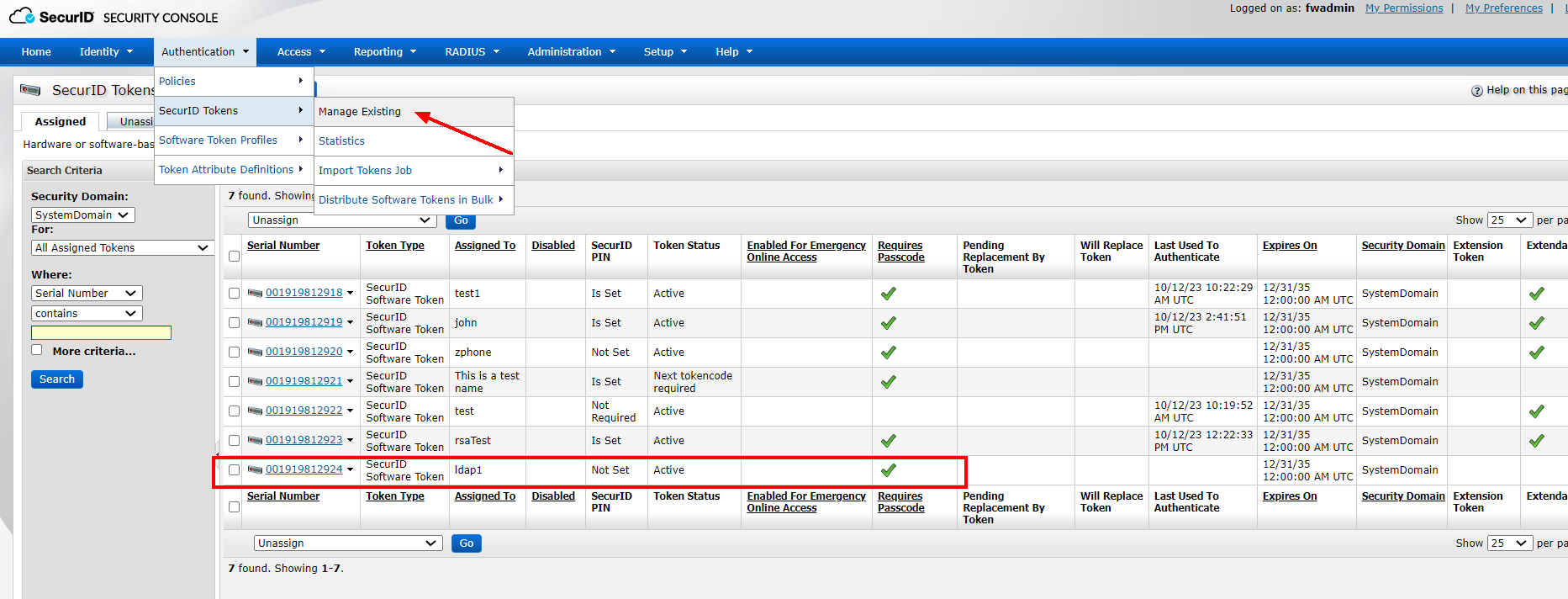
3) Create a PIN
The created user ldap1 logs in to the SecurID self-service console, https:ip/ssc
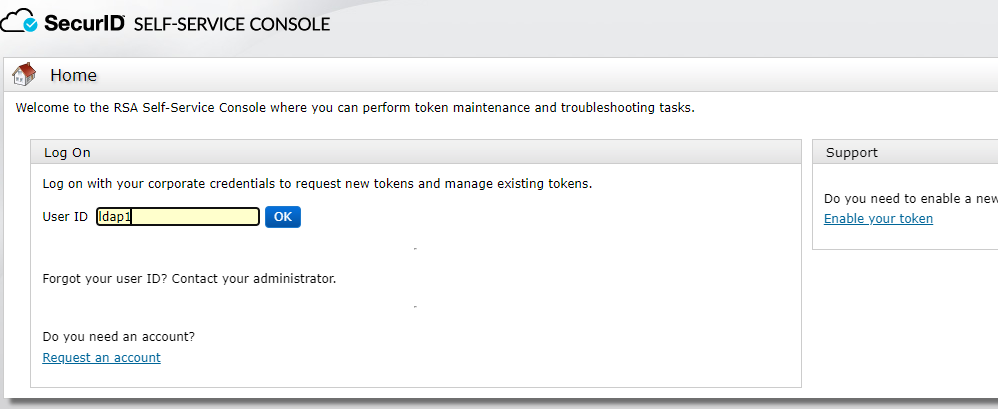
You can choose password or passcode login, LDAP1 does not set passcode, so choose password login here. In the Security Console, Identity>Users>Manage Existing> user ldap1> Set the passcode in the Authentication settings
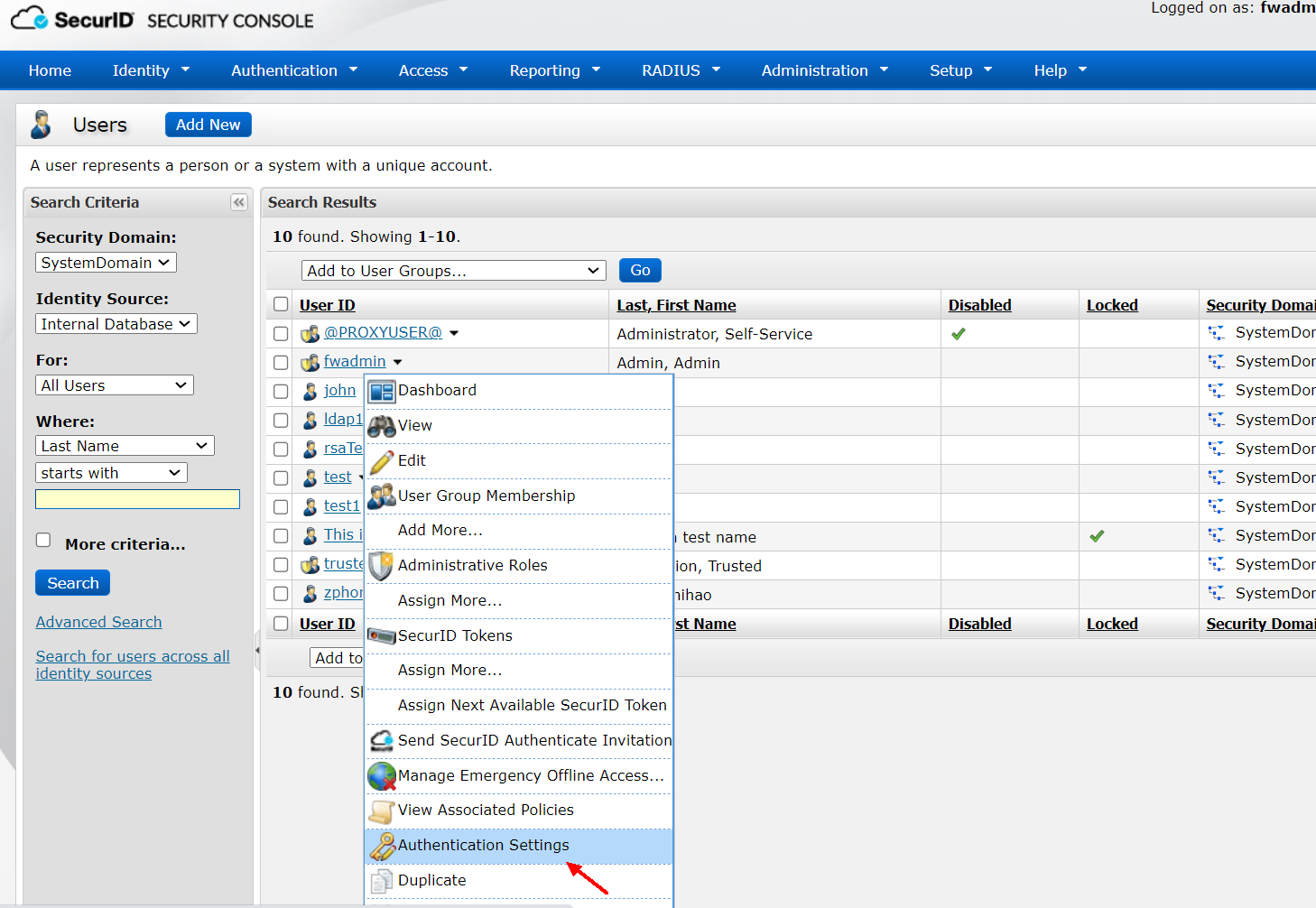
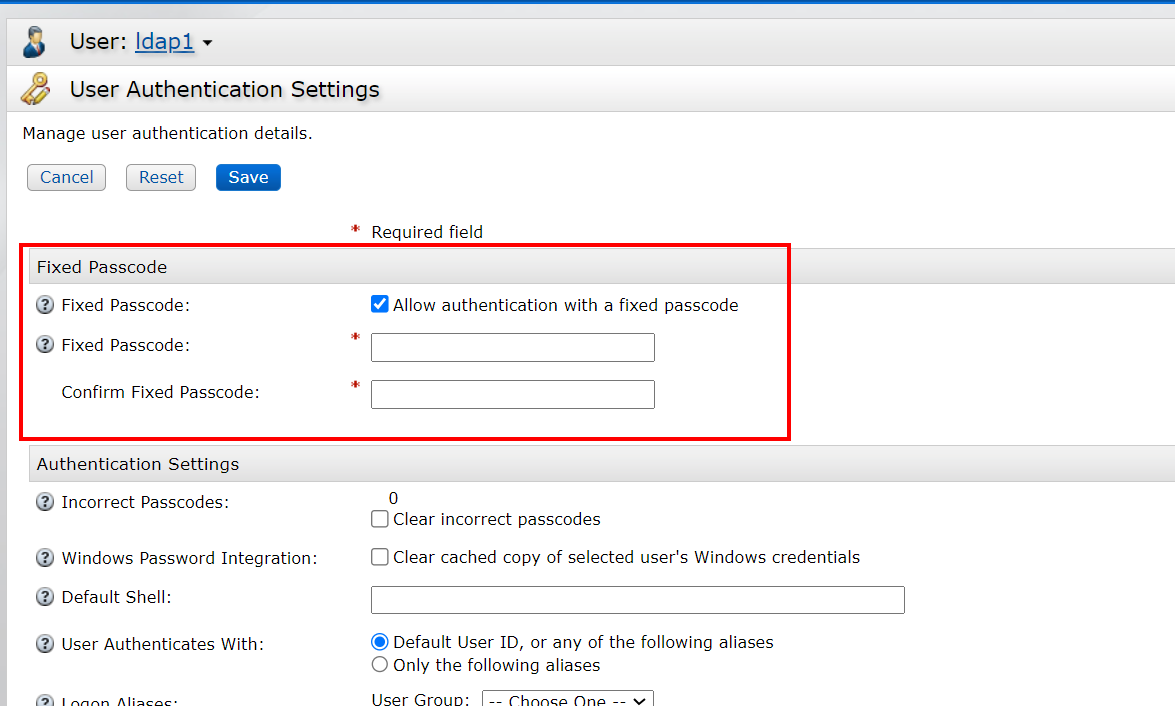
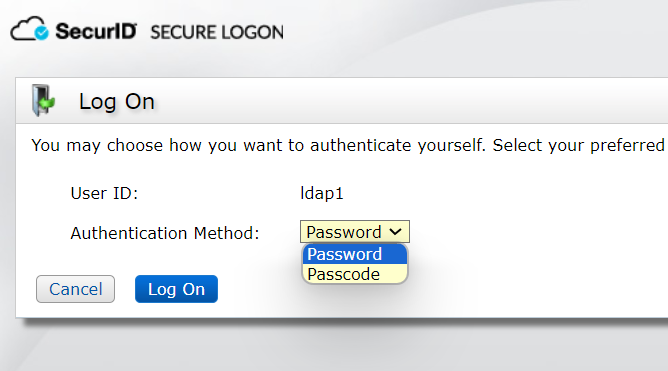
After the ssc login is successful, click create PIN on the left, the PIN created here is the PIN used for subsequent logins, set here to 1234
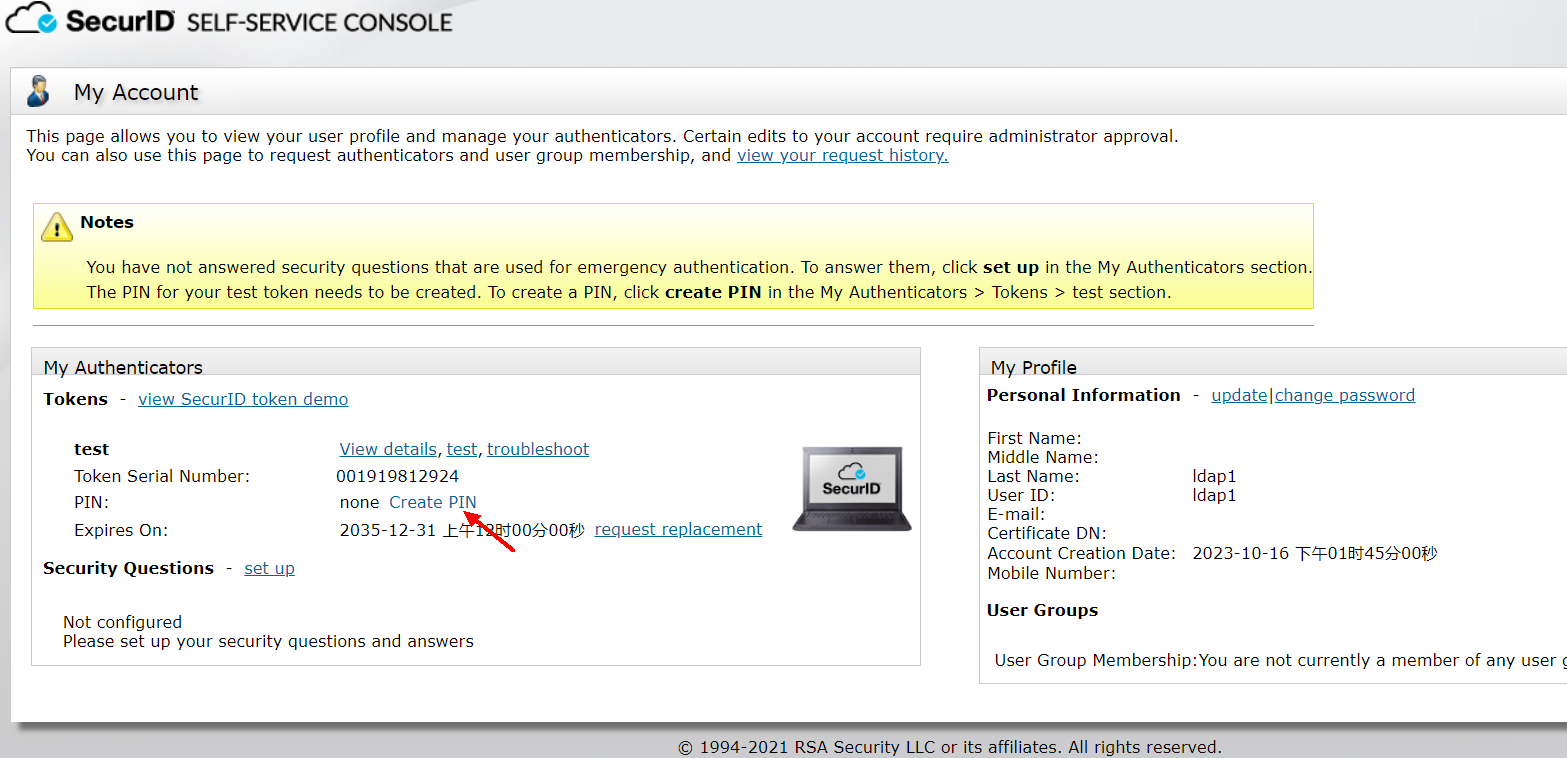
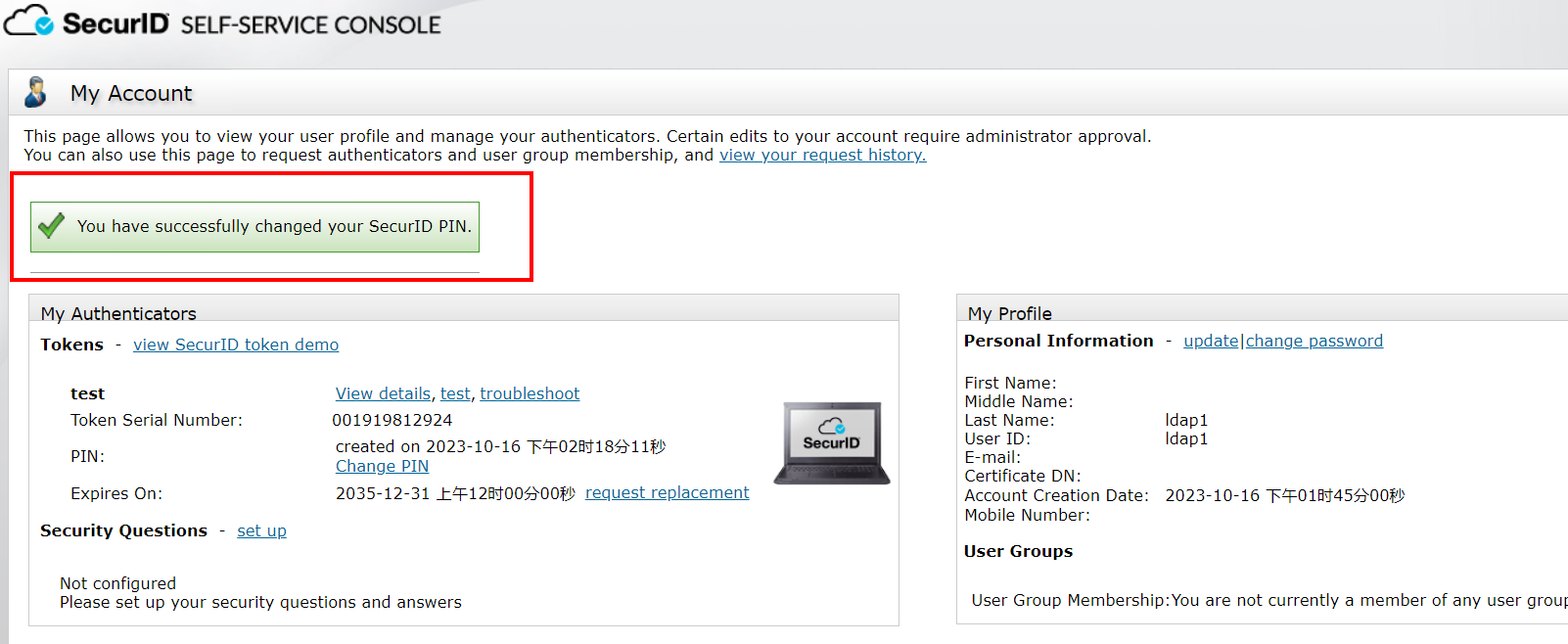
4) Click the user’s token >Distribute to assign a token profile to Token
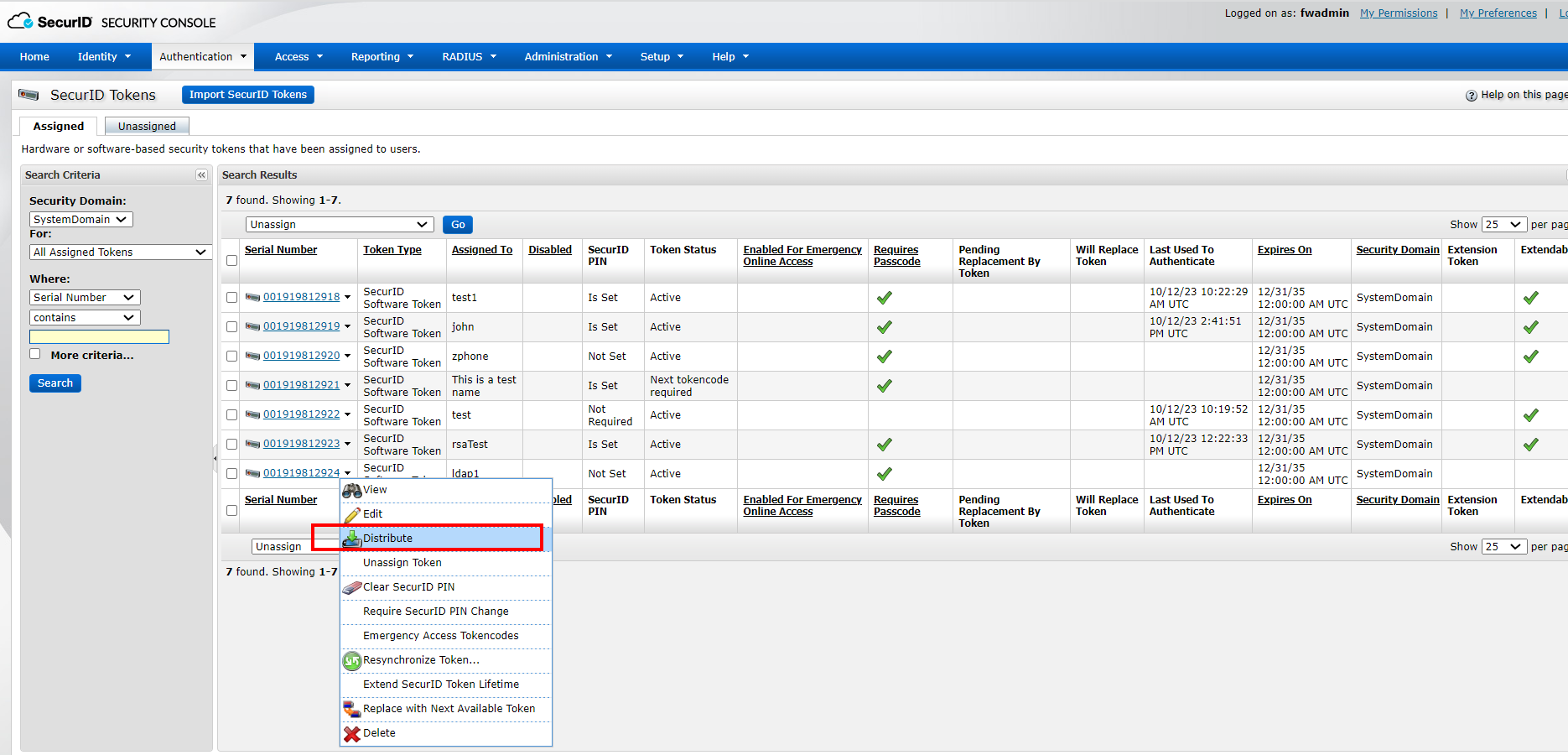
Select the Token Profile you just created, save&distribute
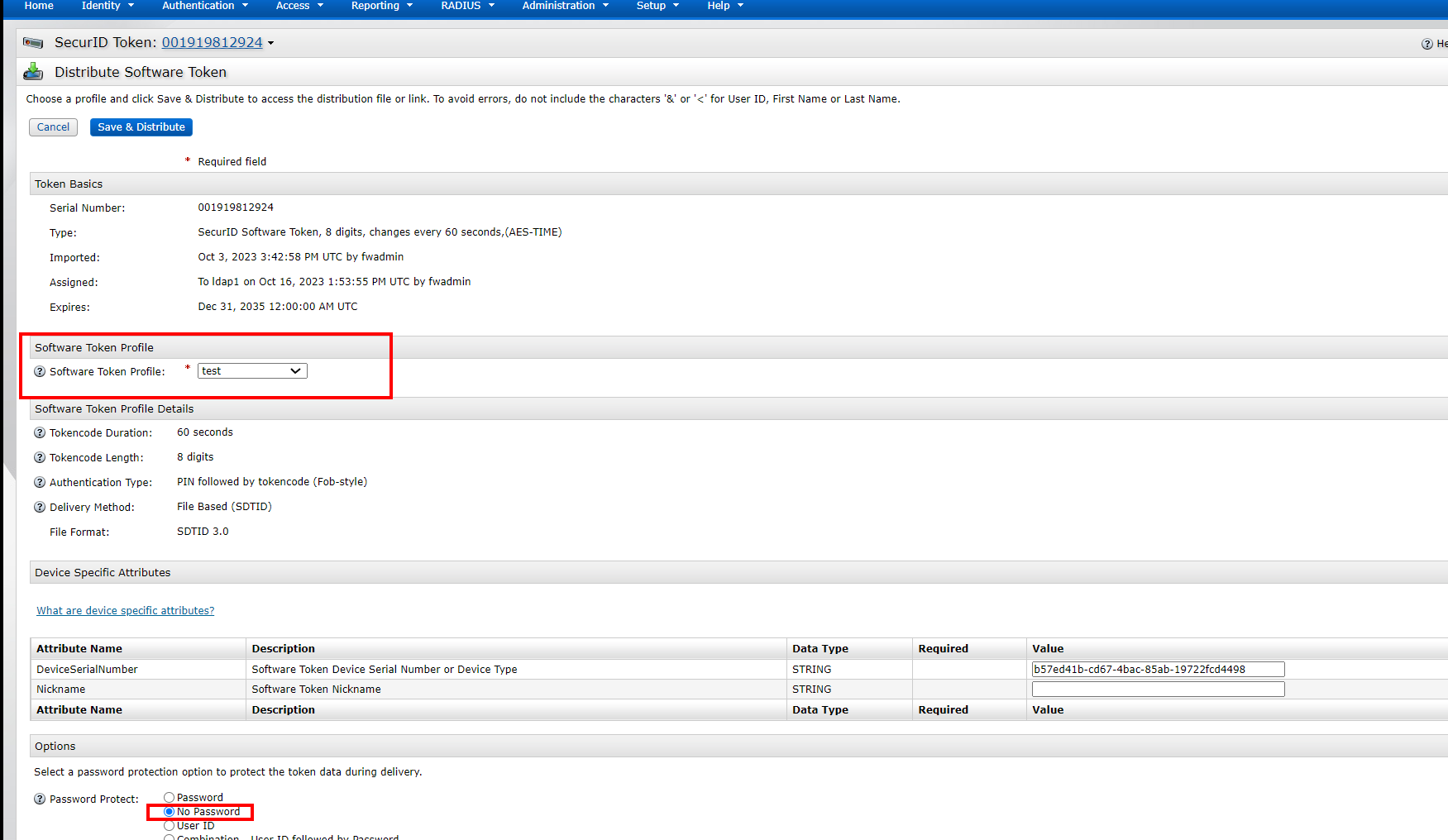
Download the Token file, unzip it and import it into the RSA SecurID Token software
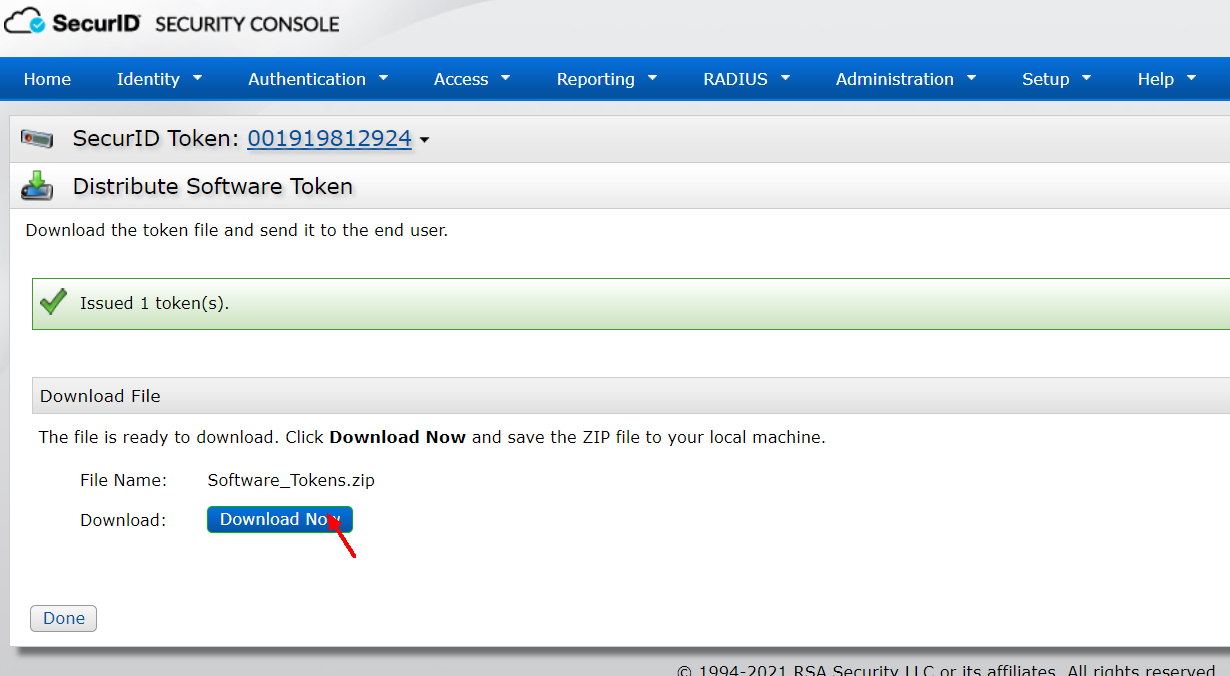
Open the RSA Token software and import the token file you just downloaded
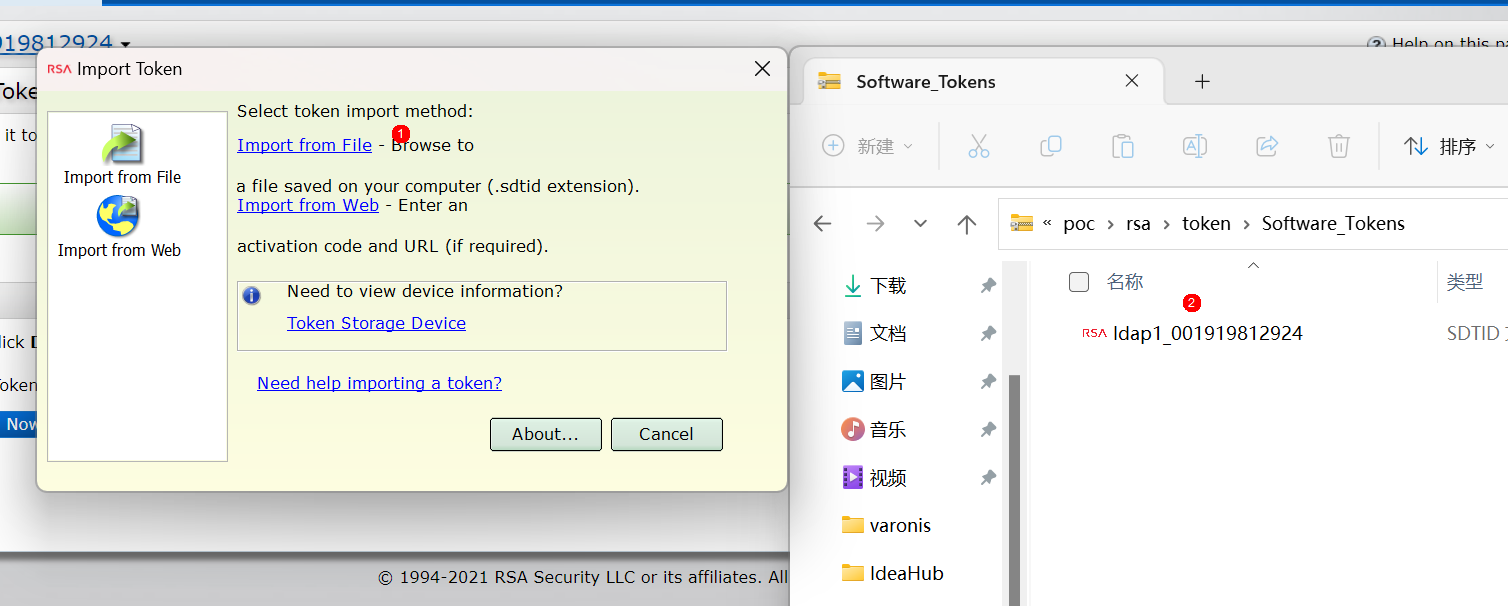
After the import is complete, the RSA software will display the Tokencode, which is the Token that needs to be entered when logging in
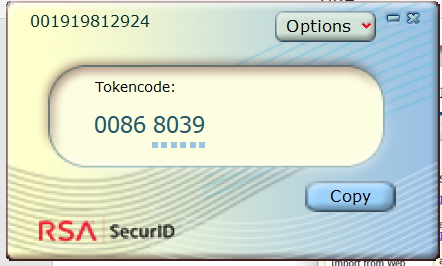
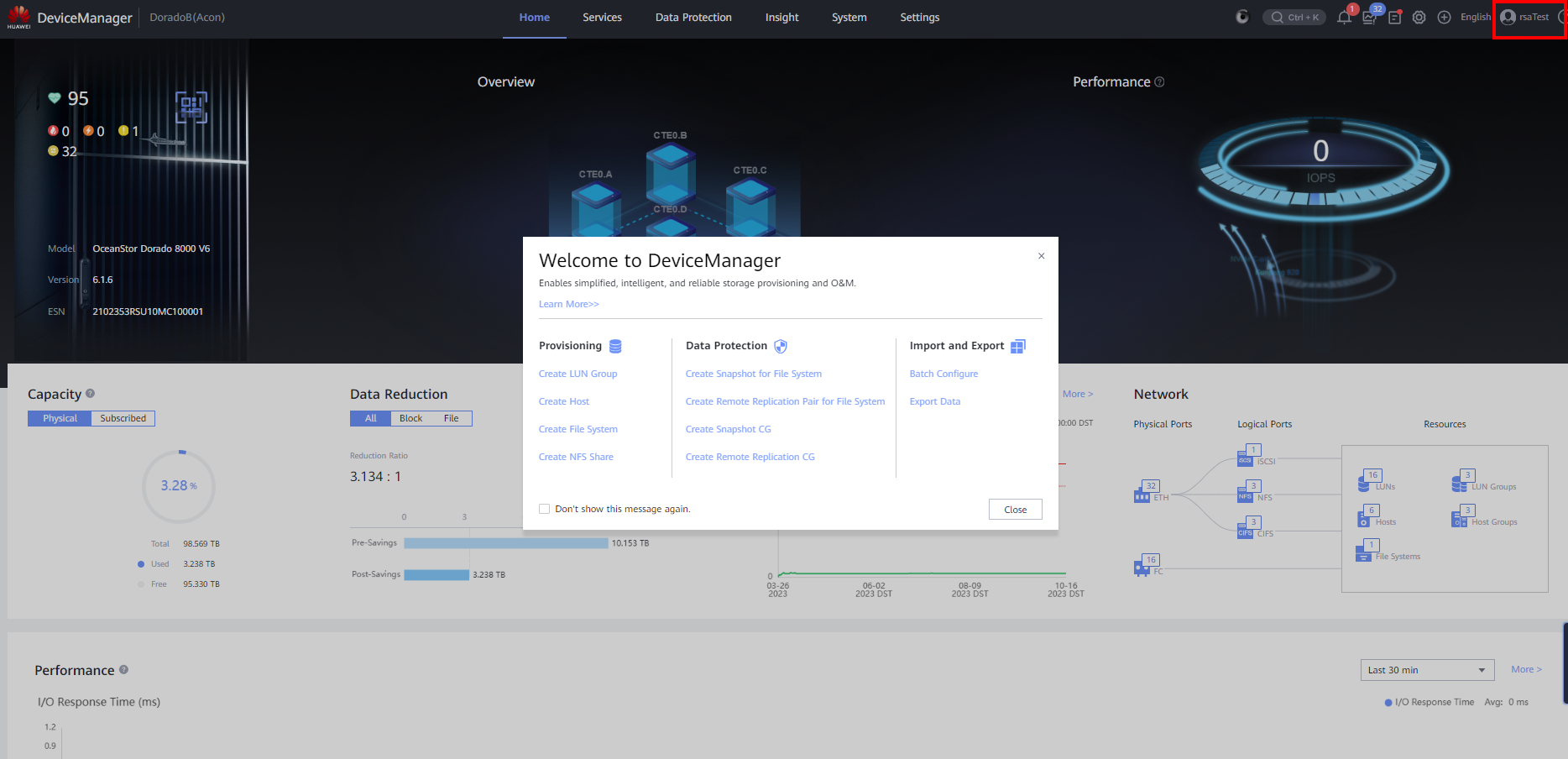
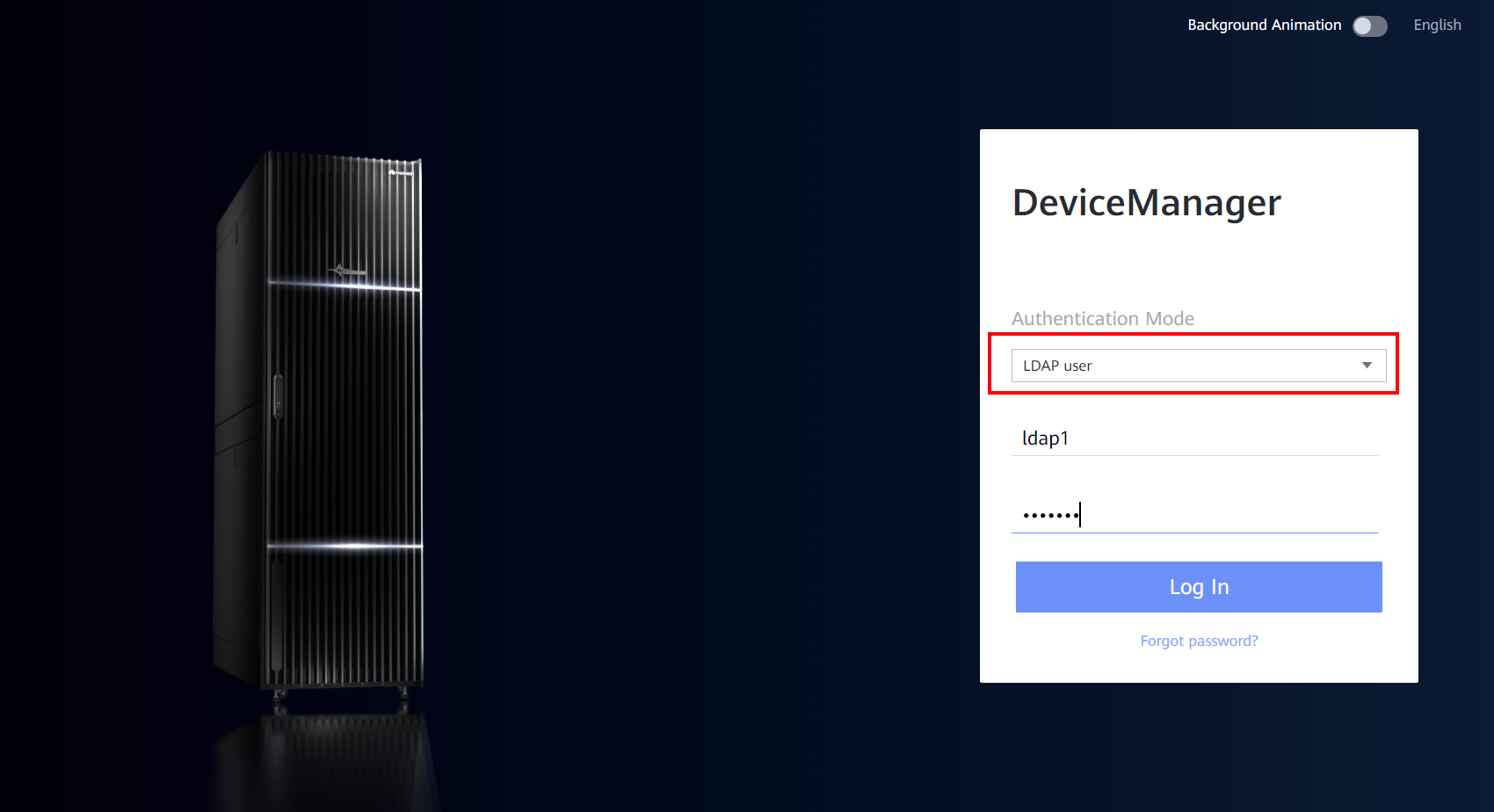
5) DeviceManager login
Log in as LDAP user, enter the LDAP user password, and log in
Enter the PIN and Tokencode in the RADIUS dynamic password
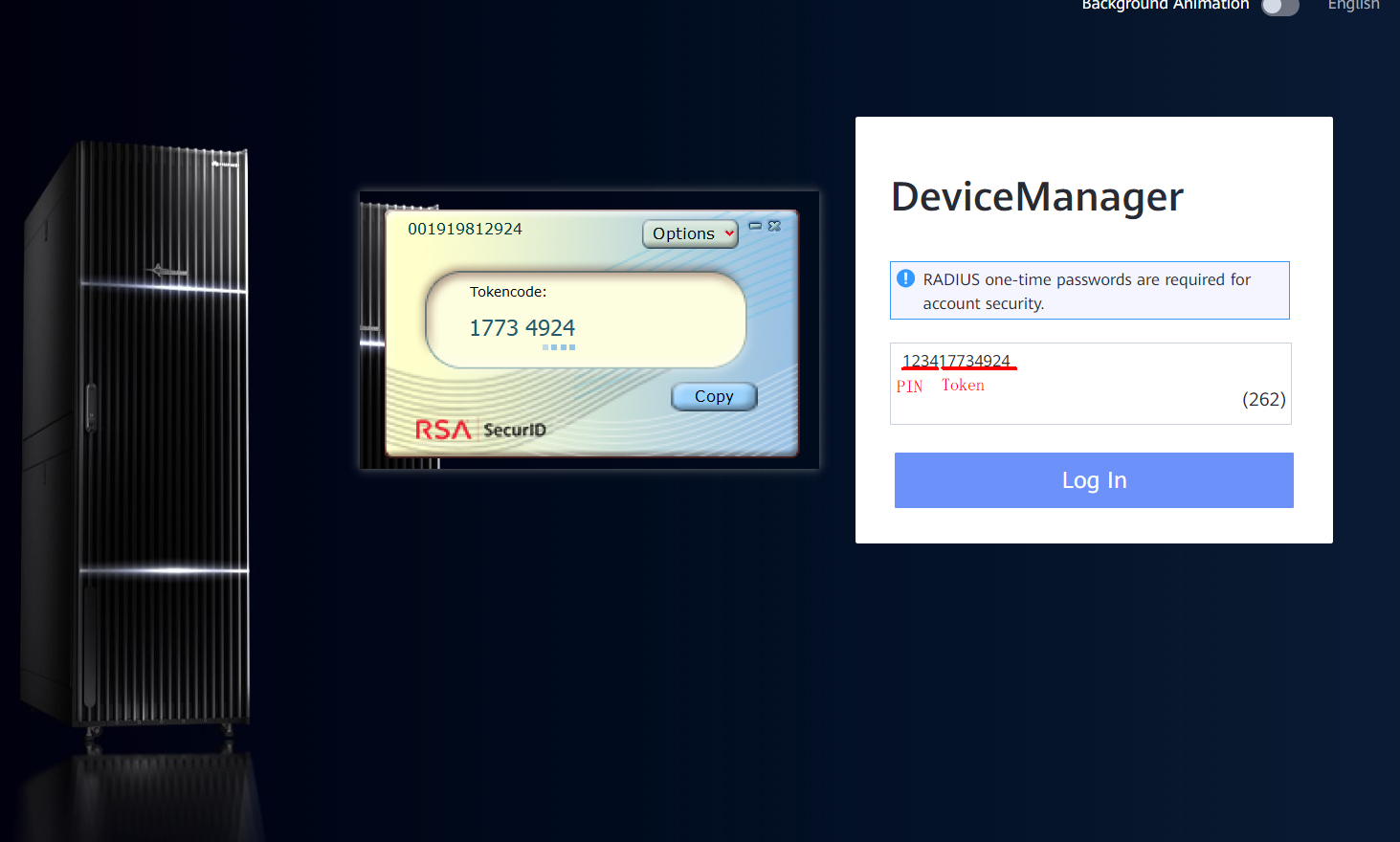
Login successful:
3.4 RADIUS login by SecureID+ TOKEN
- Create a RADIUS user in RSA Security Console and DeviceManager, both users have the same name, and the user created here is test
- RSA Security Console assigns a token to the user, same as 3.3
- Select the corresponding token > Distribute, the Token Profile selected here is different from that in 3.3.
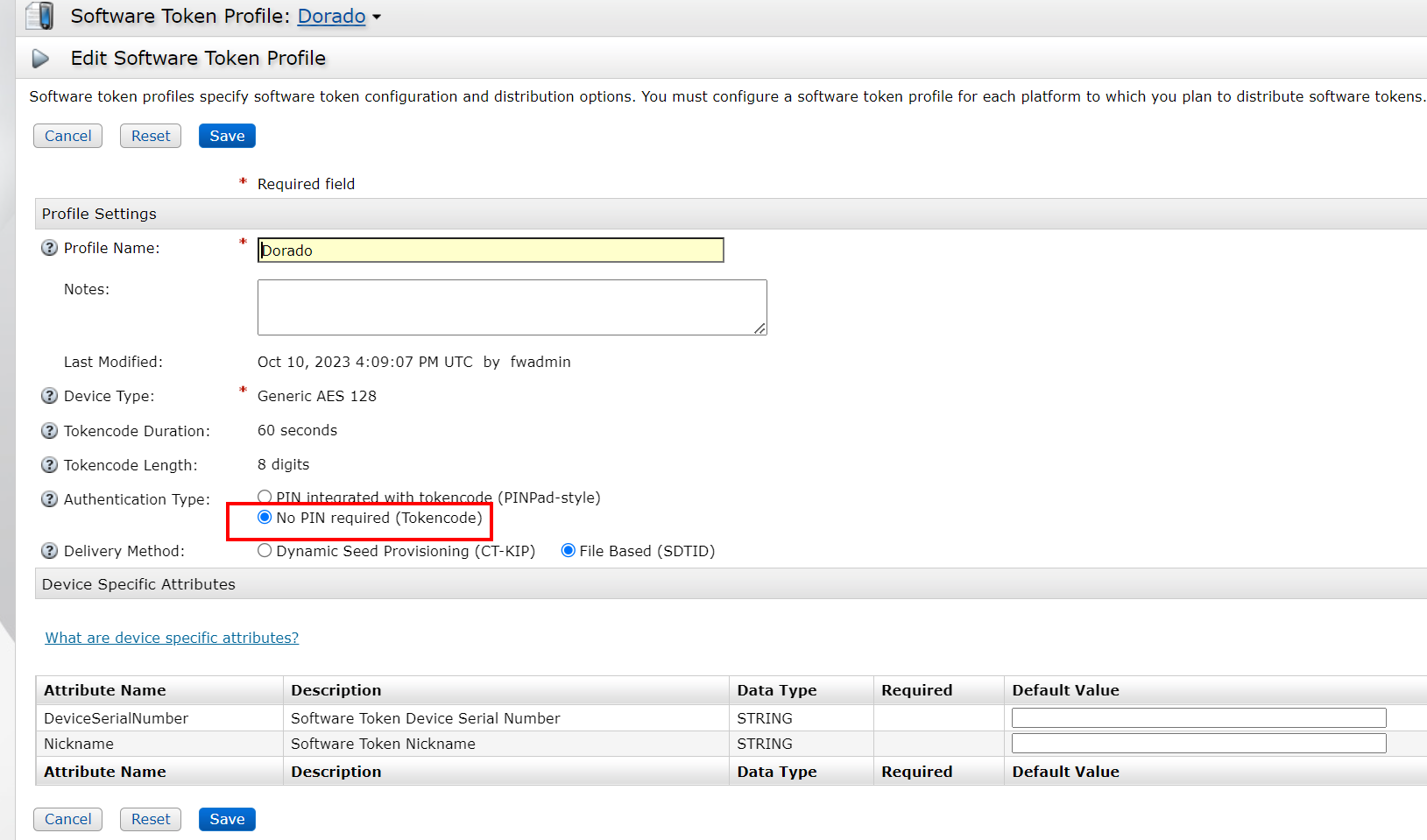
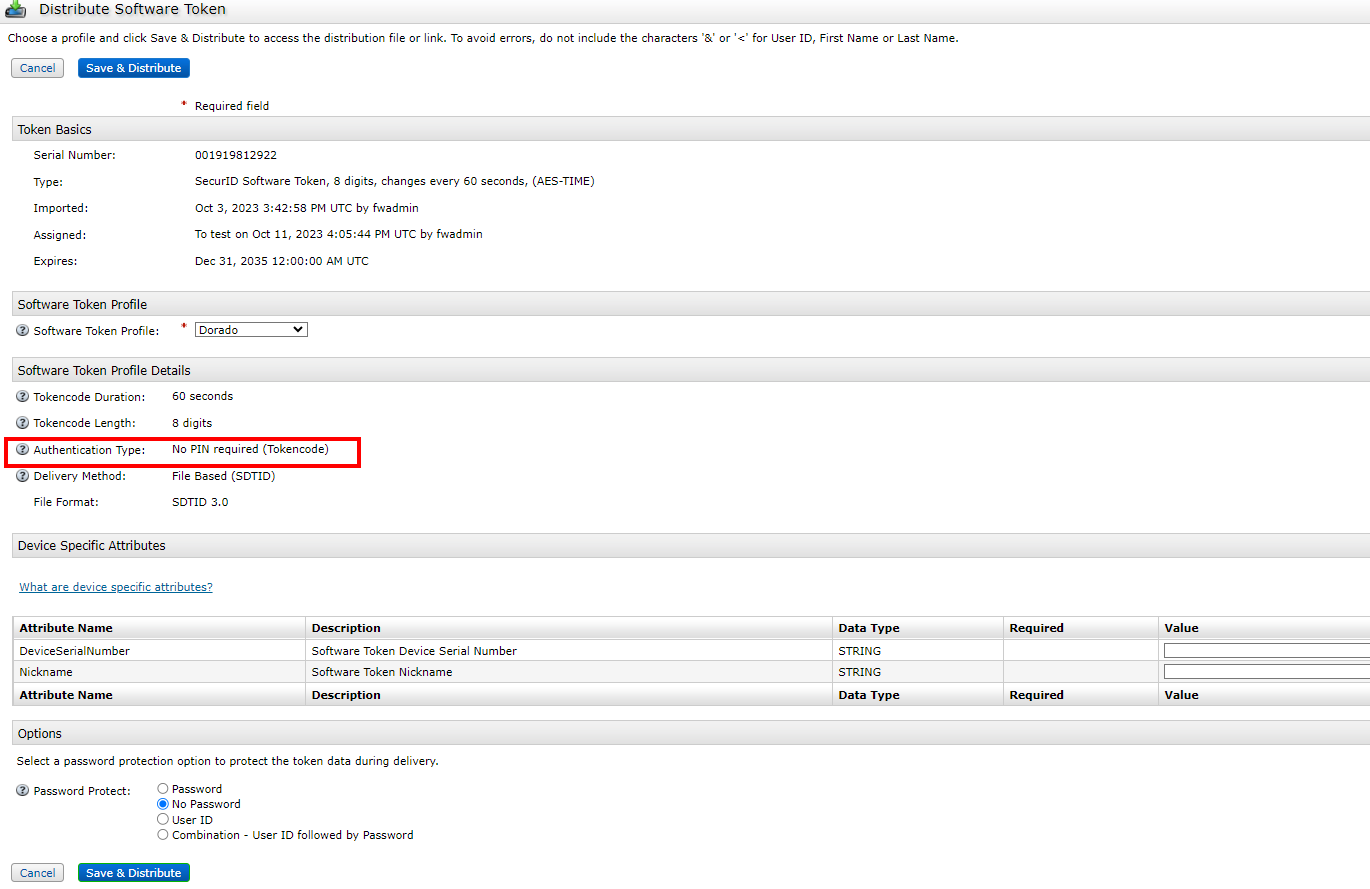
4) save&distribute, download the corresponding token file
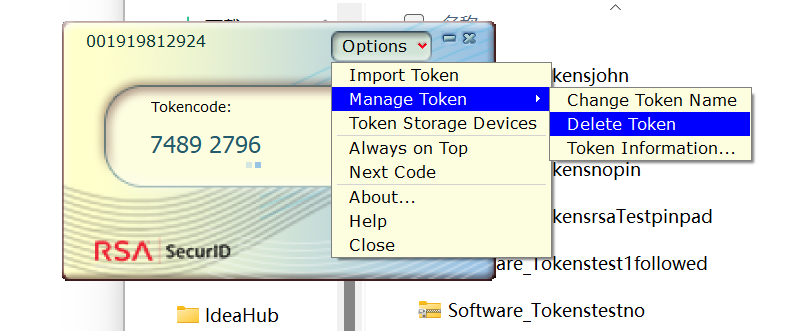
5) Import Token, Manage Token>Delete Token First delete the existing token, and then Import Token
6) Log in to DeviceManager, select RADIUS user as the login method, and enter the password into Token
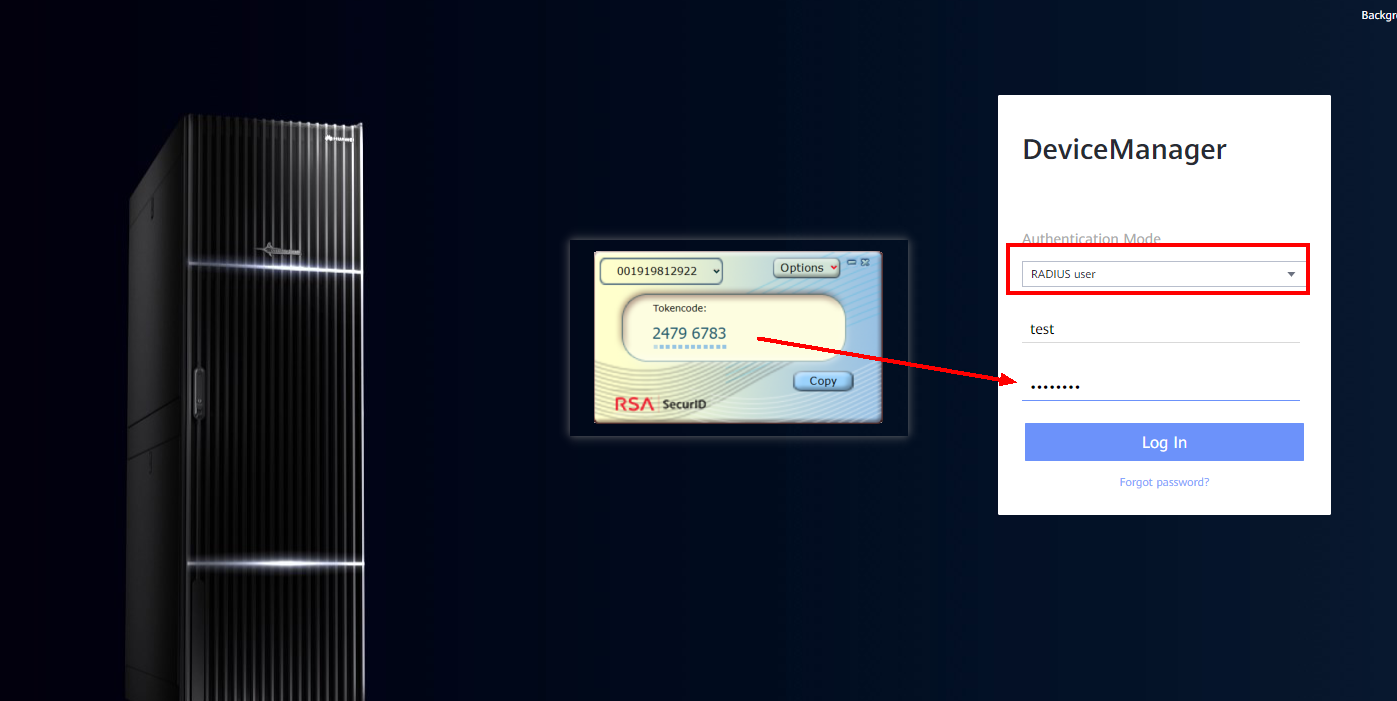
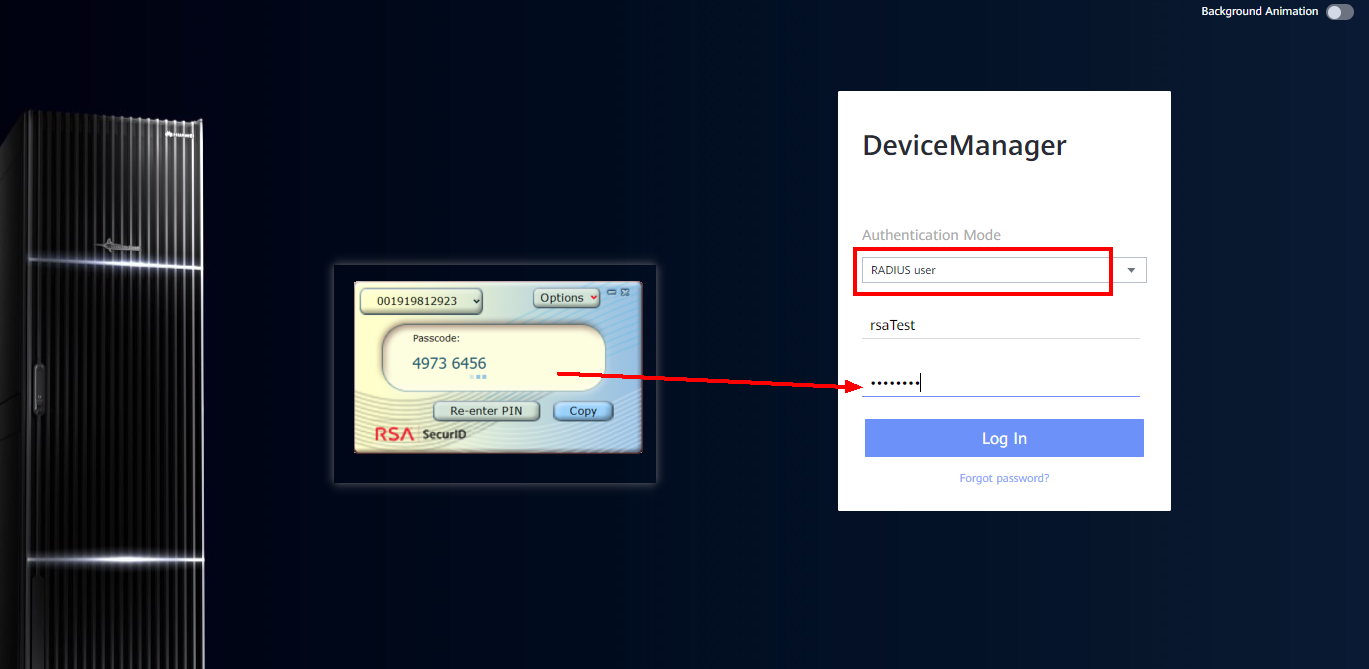
3.5 RADIUS login by SecureID+ PINPad
1) Create a RADIUS user in RSA Security Console and DeviceManager, the two users have the same name, and the user created here is rsaTest
2) RSA Security Console assigns a token to the user, same as 3.3.
3) The ssc page creates a PIN for the user, same as 3.3, set here to 1234.
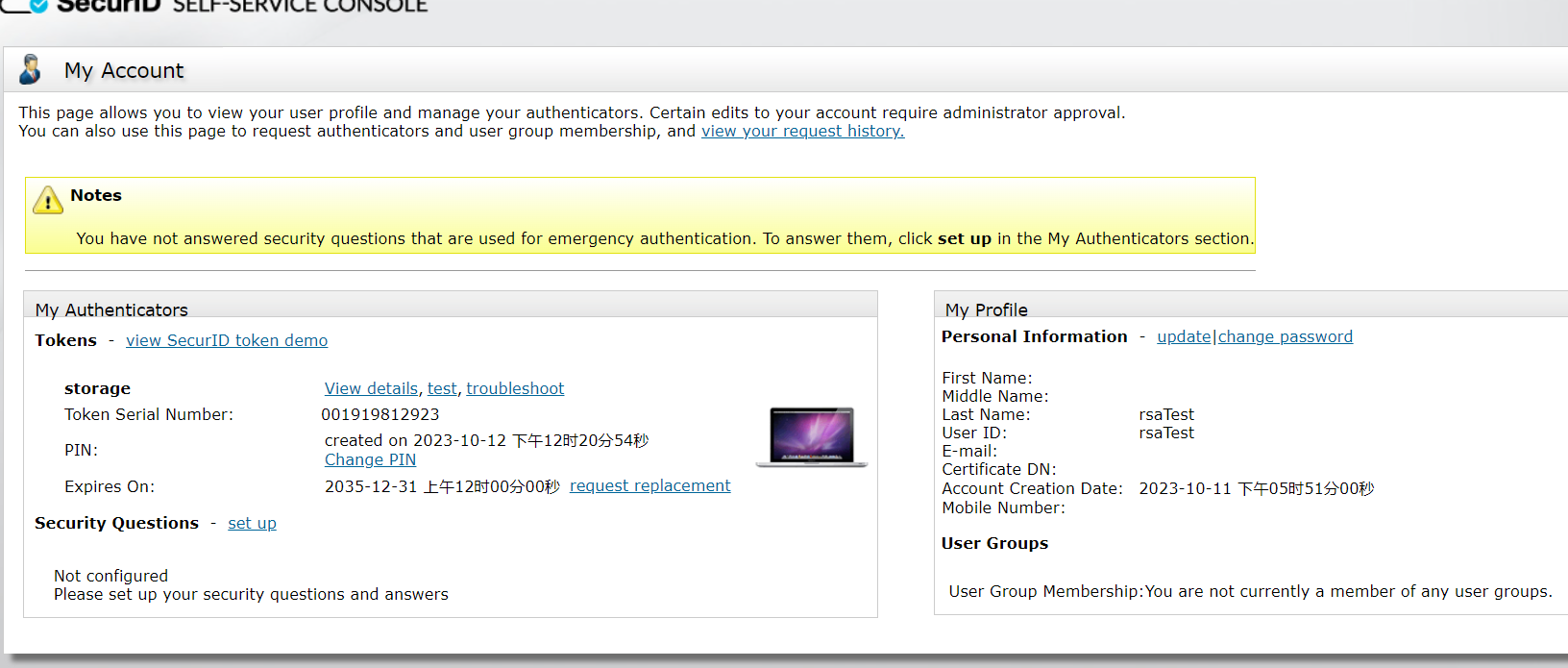
4) Select the corresponding token > Distribute, the Token Profile selected here is different from 3.3.
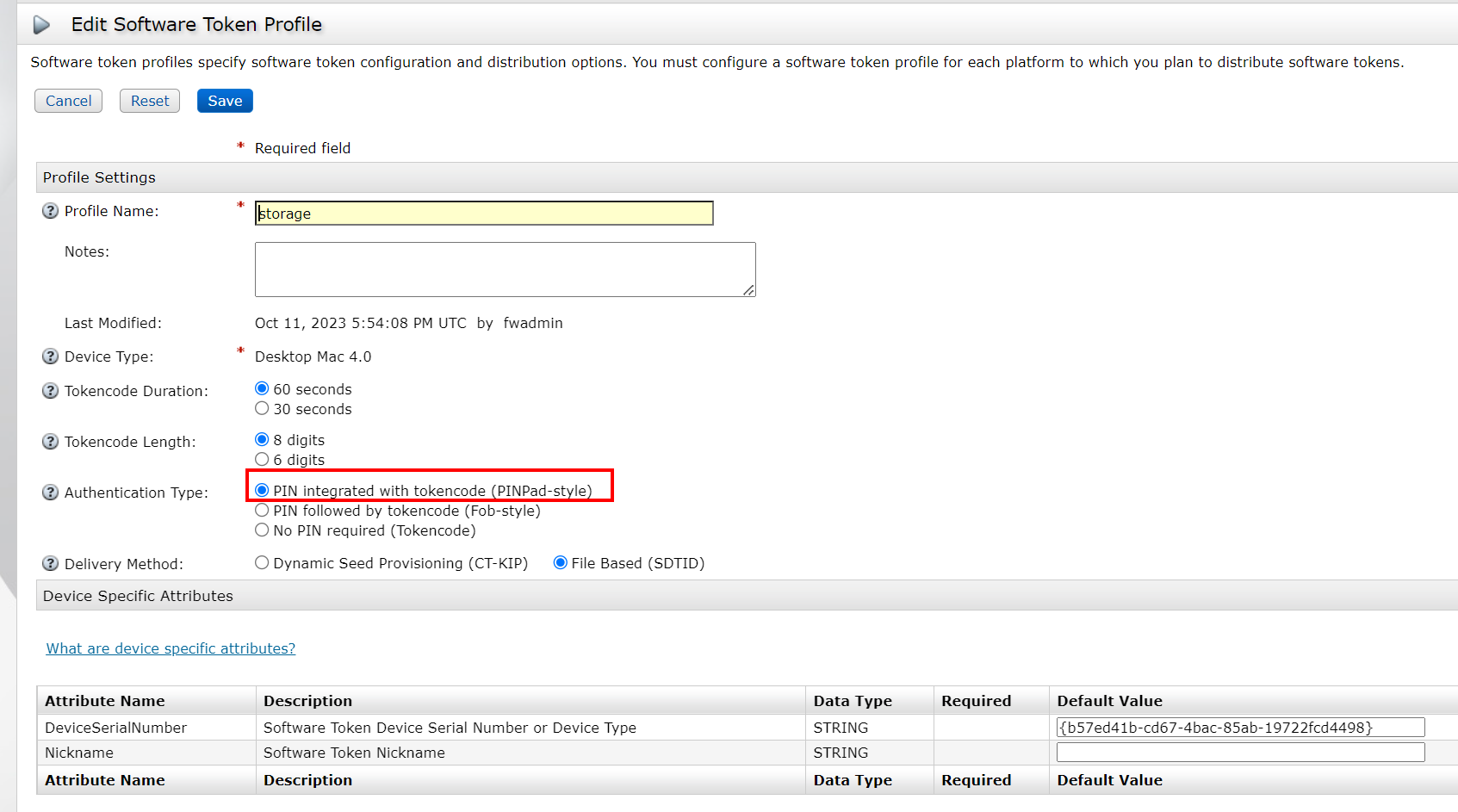
5) Assign the corresponding token profile, note that the serialnumber needs to be consistent with the device type found by the RSA software. save&distribute, download the corresponding token file
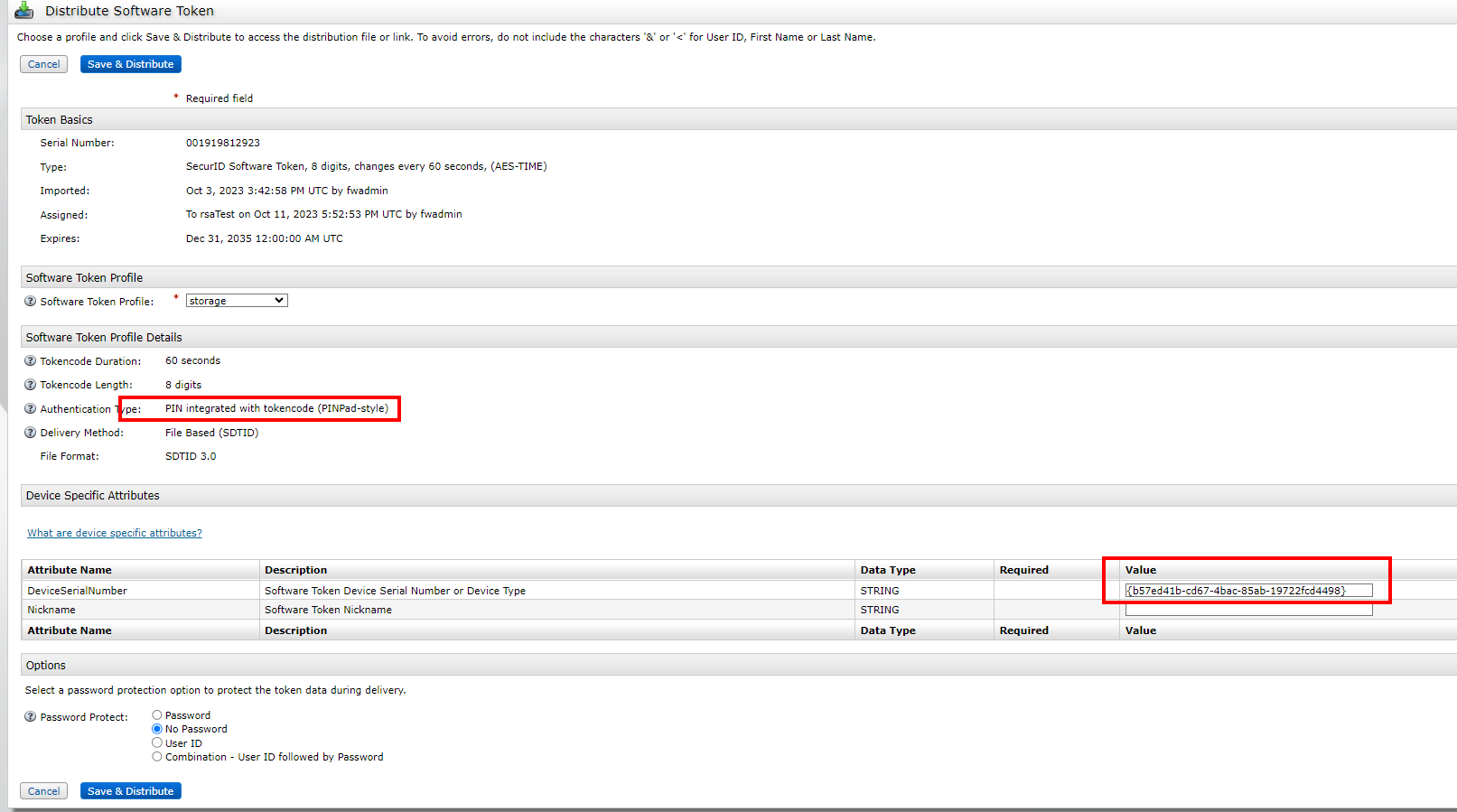
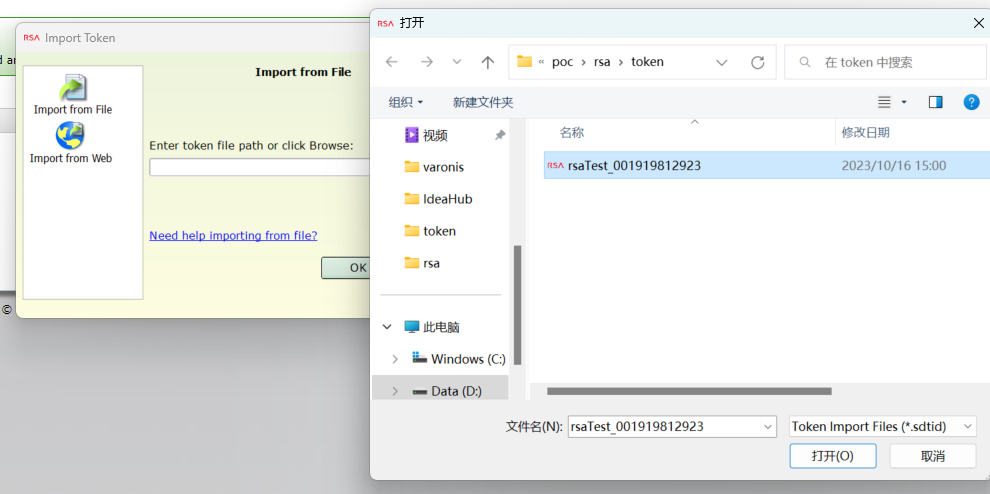
5) Import Token, Manage Token>Delete Token First delete the existing token, and then Import Token
The PINpad method requires entering a PIN first, and then the RSA software generates a passcode
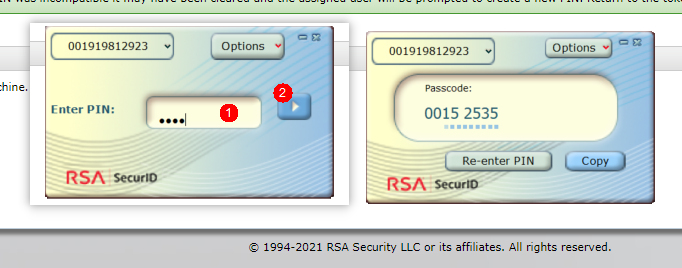
6) Log in to DeviceManager, select RADIUS user as the login method, and enter the password into Passcode